Yossi Oren
Twitter: @yossioren
Research Interests
Implementation SecurityPublications
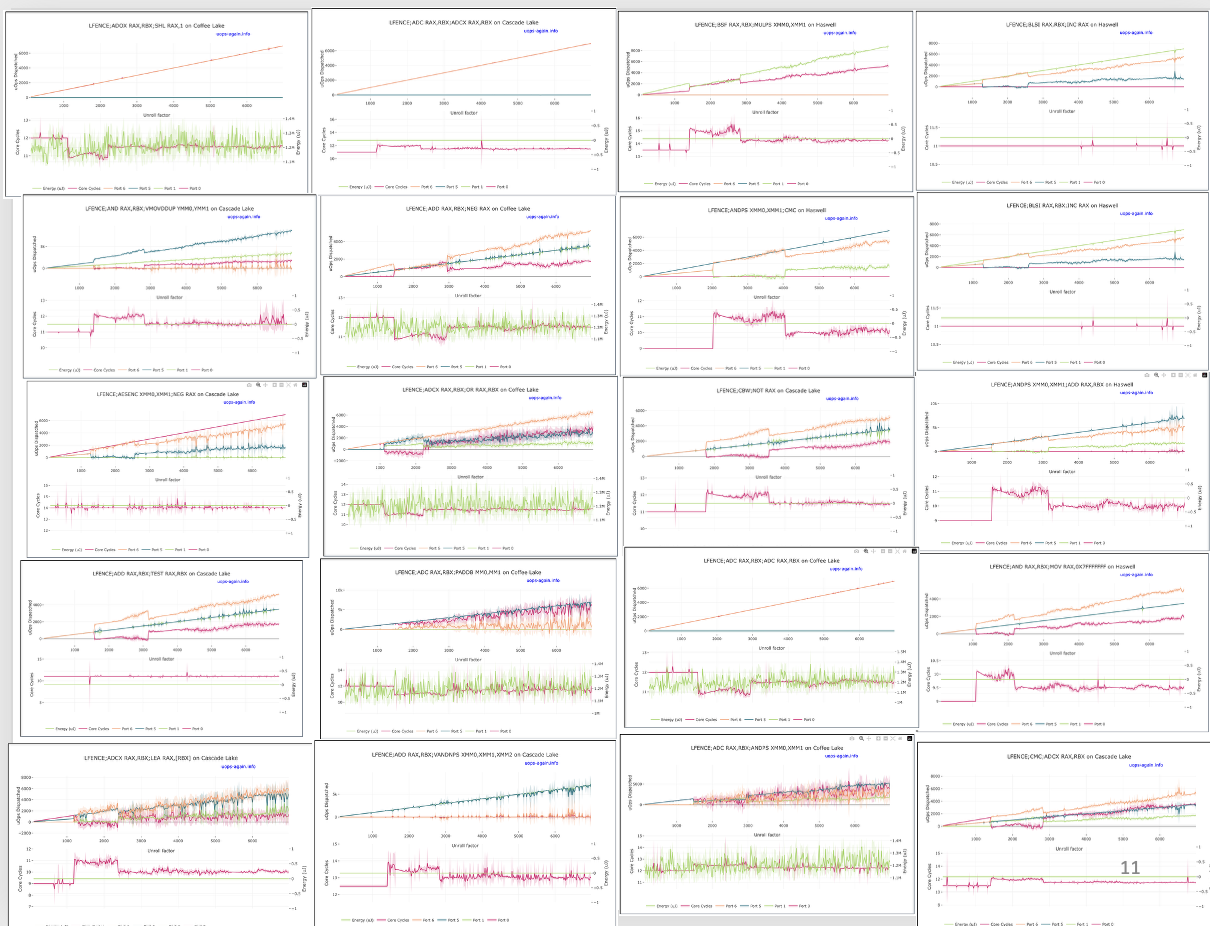
- A Second Look at Port Assignment on Intel CPUs (work in progress) (2nd Microarchitecture Security Conference, 2026)
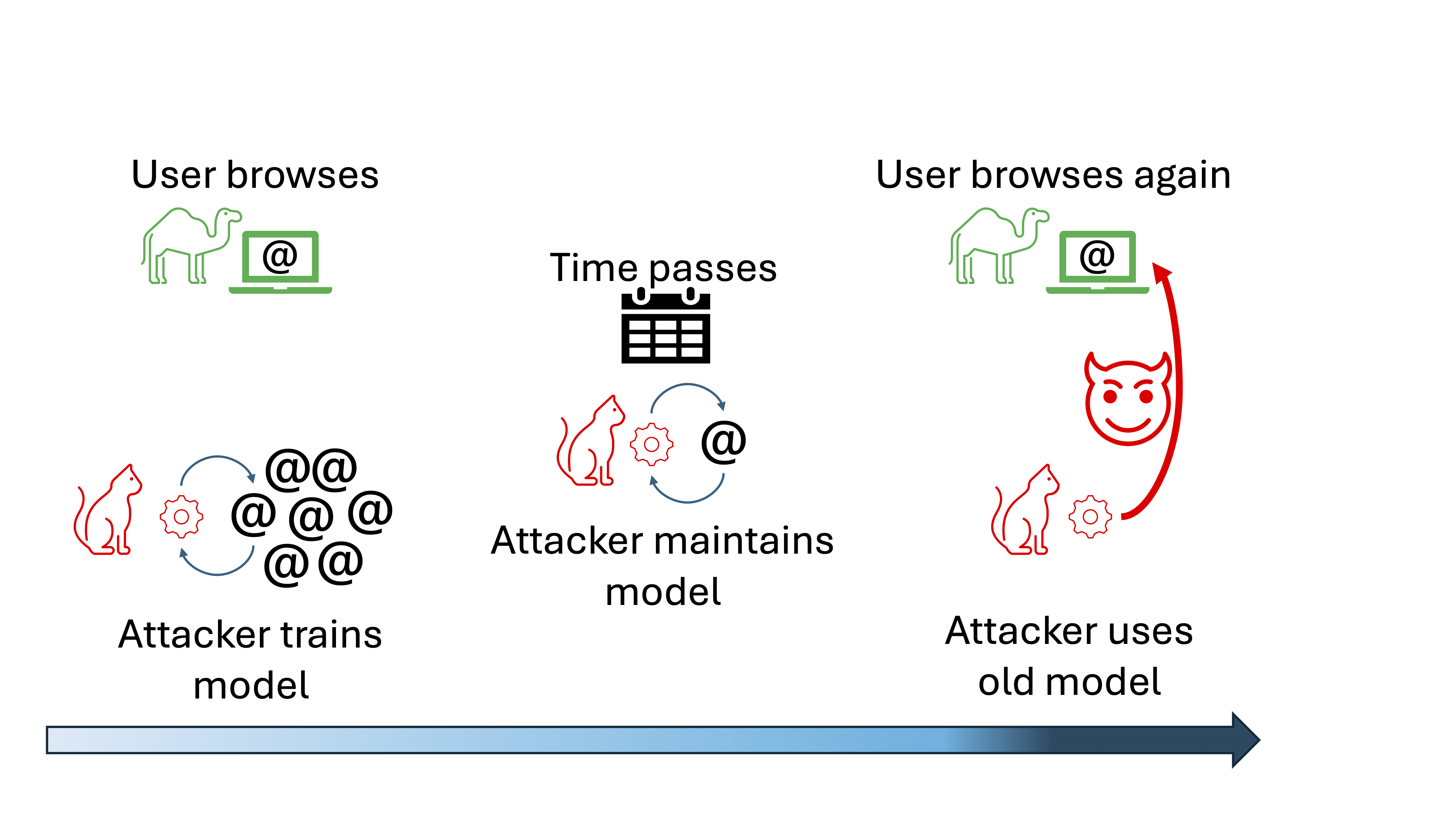
- Understanding and Addressing Concept Drift in Website Fingerprinting (Elsevier Computer Networks Journal, to appear)
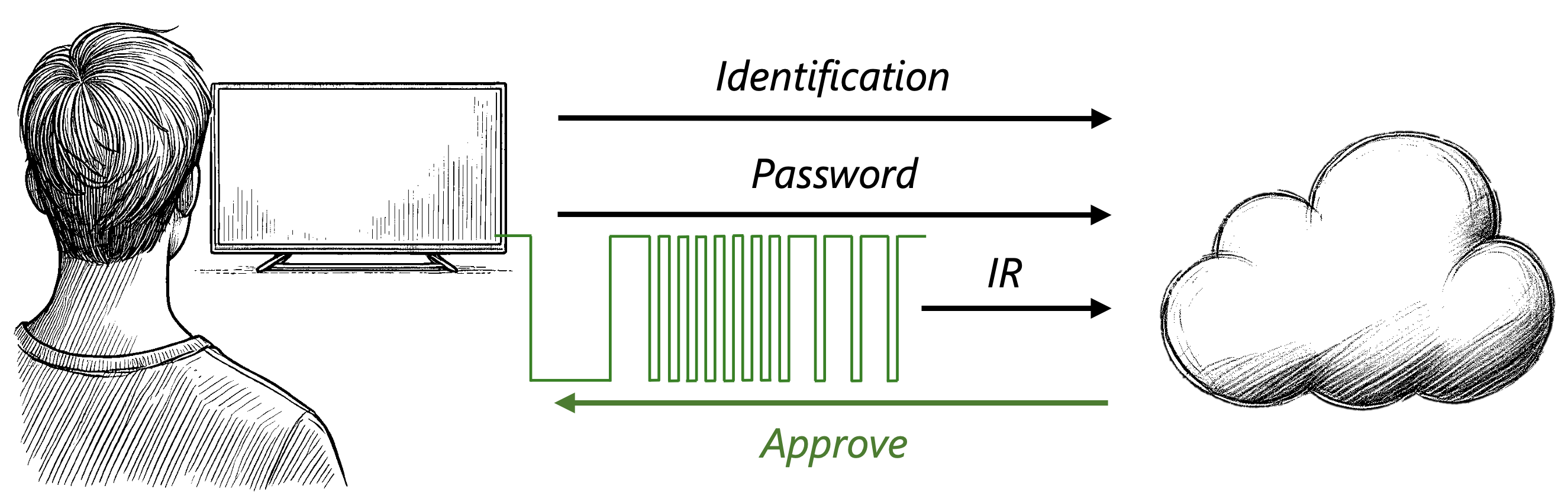
- IRIS: Enhancing the Security of IoT Devices Using Internal IR-Based Sensors (Elsevier Internet of Things Journal, Volume 34, November 2025, 101787)
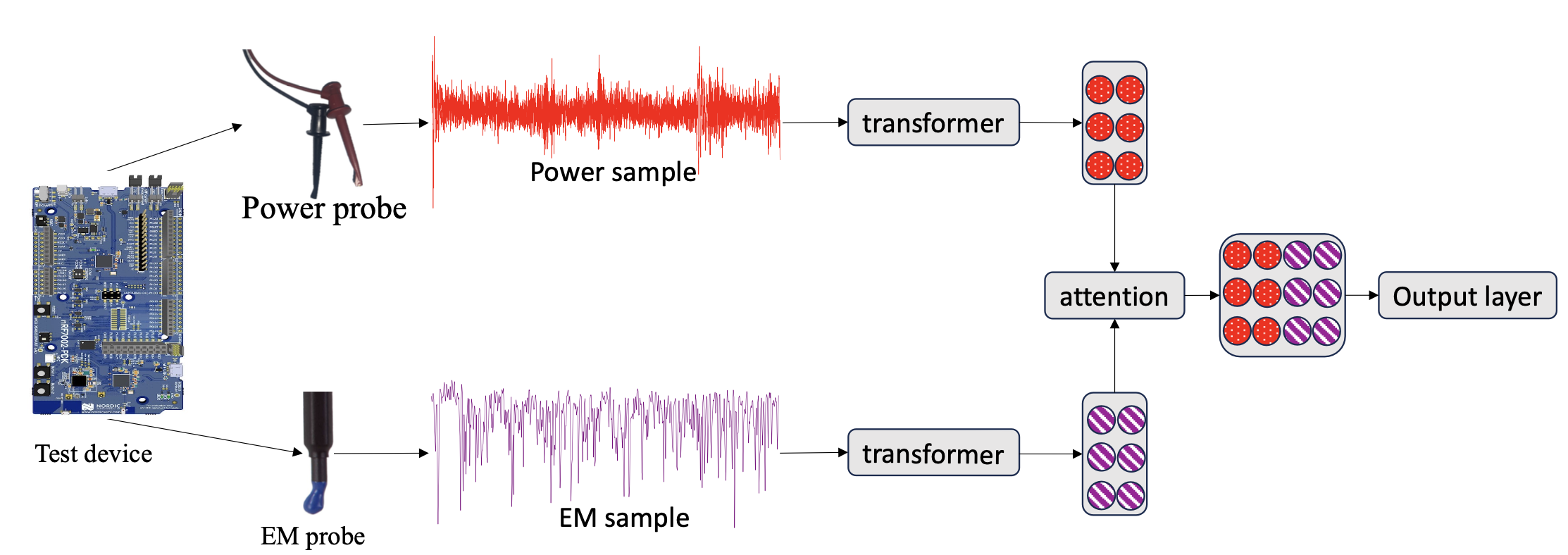
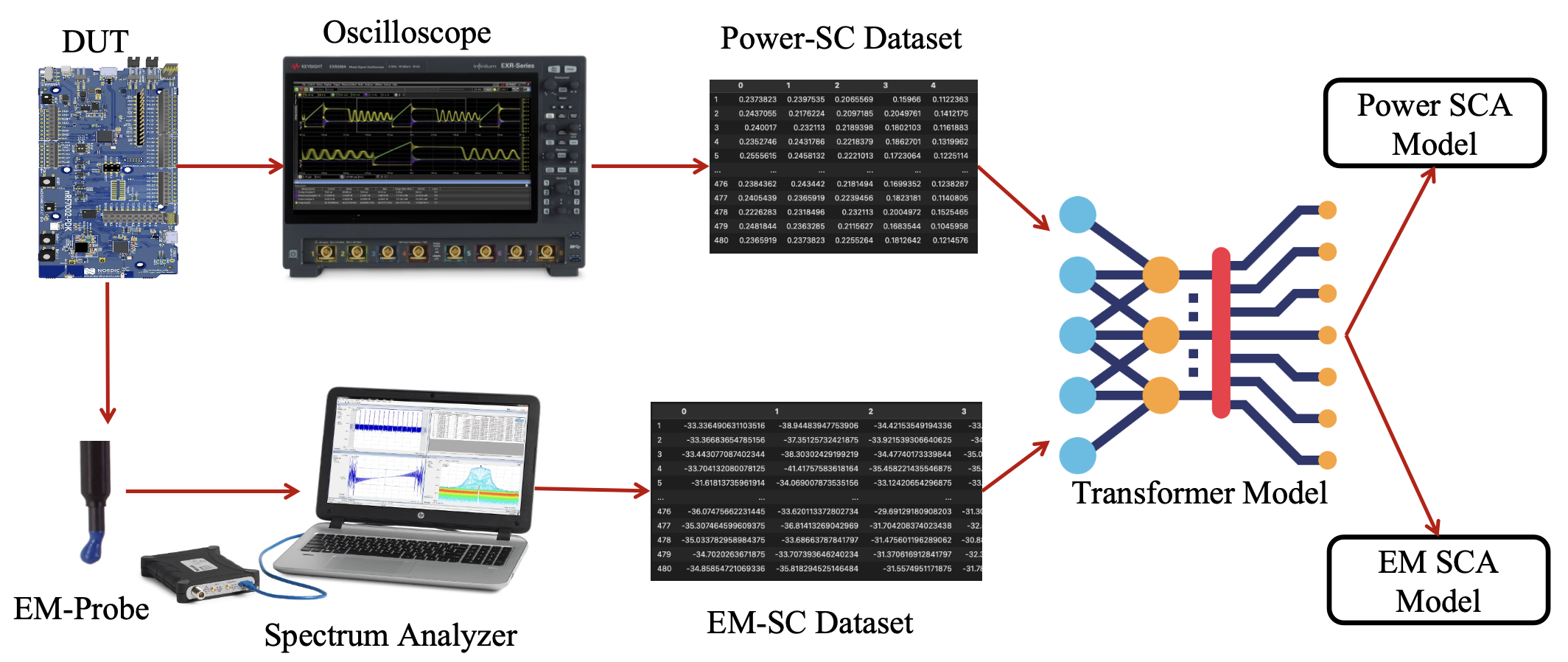
- Two's Complement: Monitoring Software Control Flow using Both Power and Electromagnetic Side Channels (27th Euromicro Conference on Digital System Design, 2024)
- Waves of Knowledge: A Comparative Study of Electromagnetic and Power Side-Channel Monitoring in Embedded Systems (EAI SmartSP 2023)
- Pixel Thief: Exploiting SVG Filter Leakage in Firefox and Chrome (33rd USENIX Security Symposium, 2024)
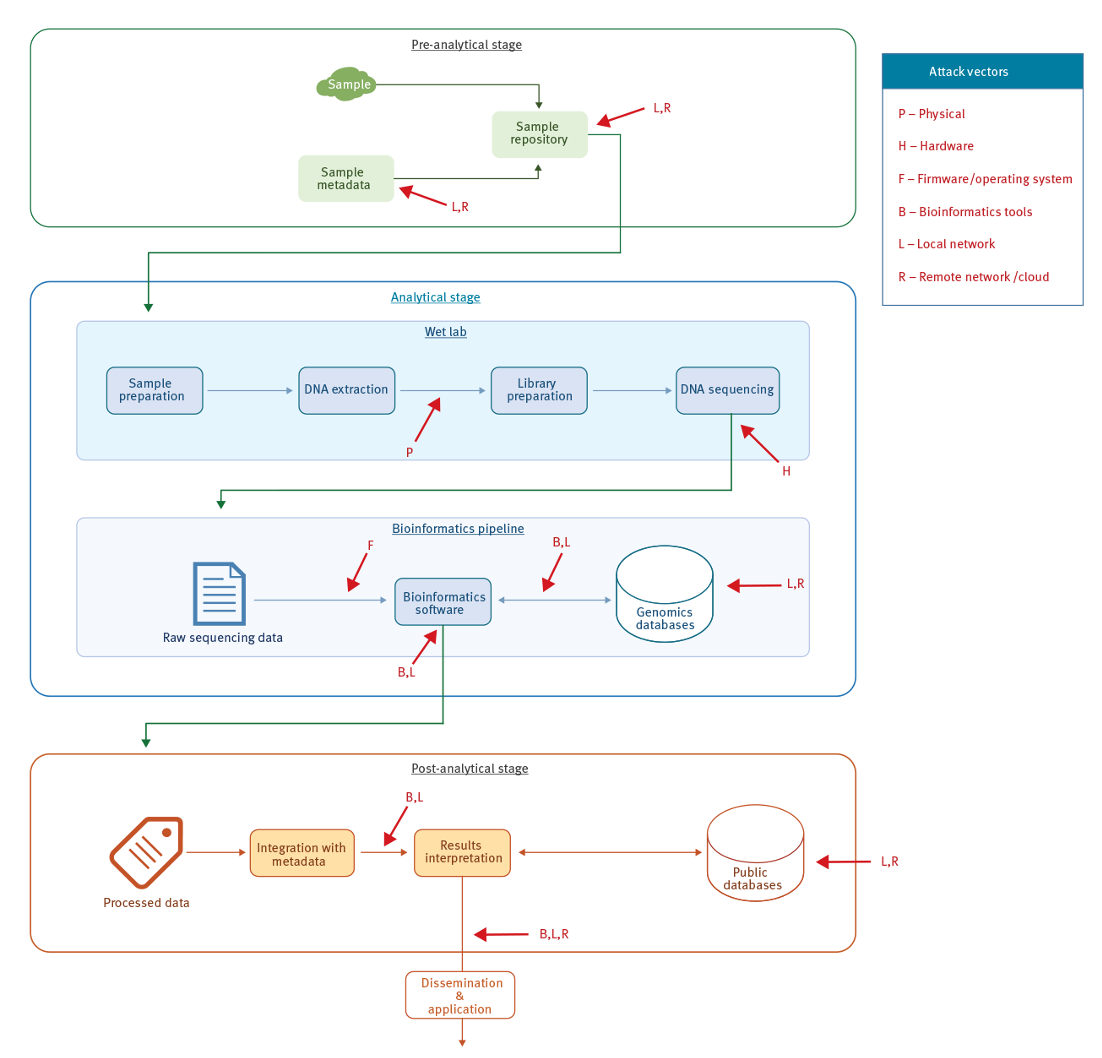
- The Attack Surface of Wet Lab Automation (Cyberbiosecurity)
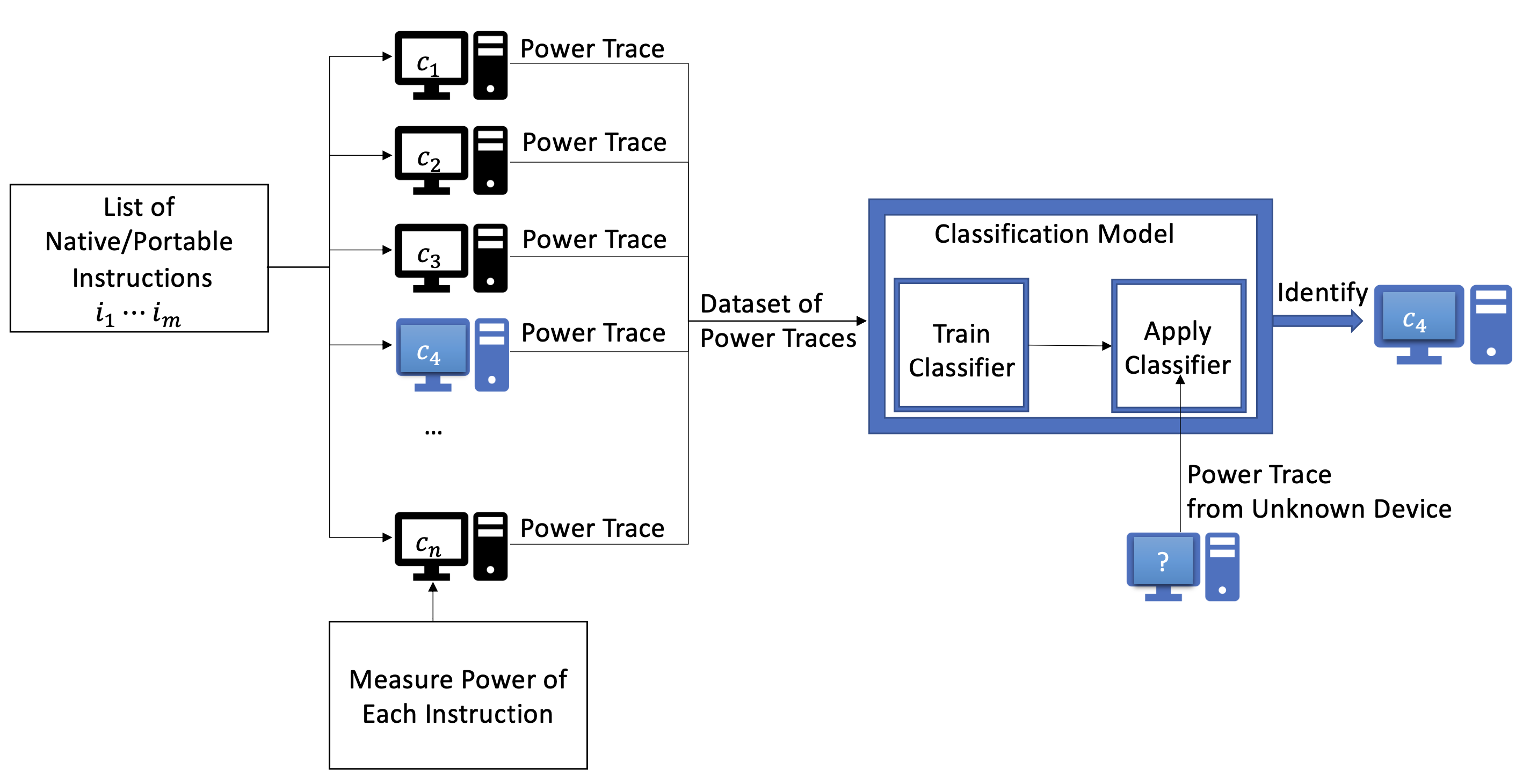
- The Finger in the Power: How to Fingerprint PCs by Monitoring their Power Consumption (20th Conference on Detection of Intrusions and Malware & Vulnerability Assessment, DIMVA 2023)
- Juliet-PUF: Enhancing the Security of IoT-Based SRAM-PUFs Using the Remanence Decay Effect (IEEE Internet of Things Journal Volume 10, Issue 14, July 2023)
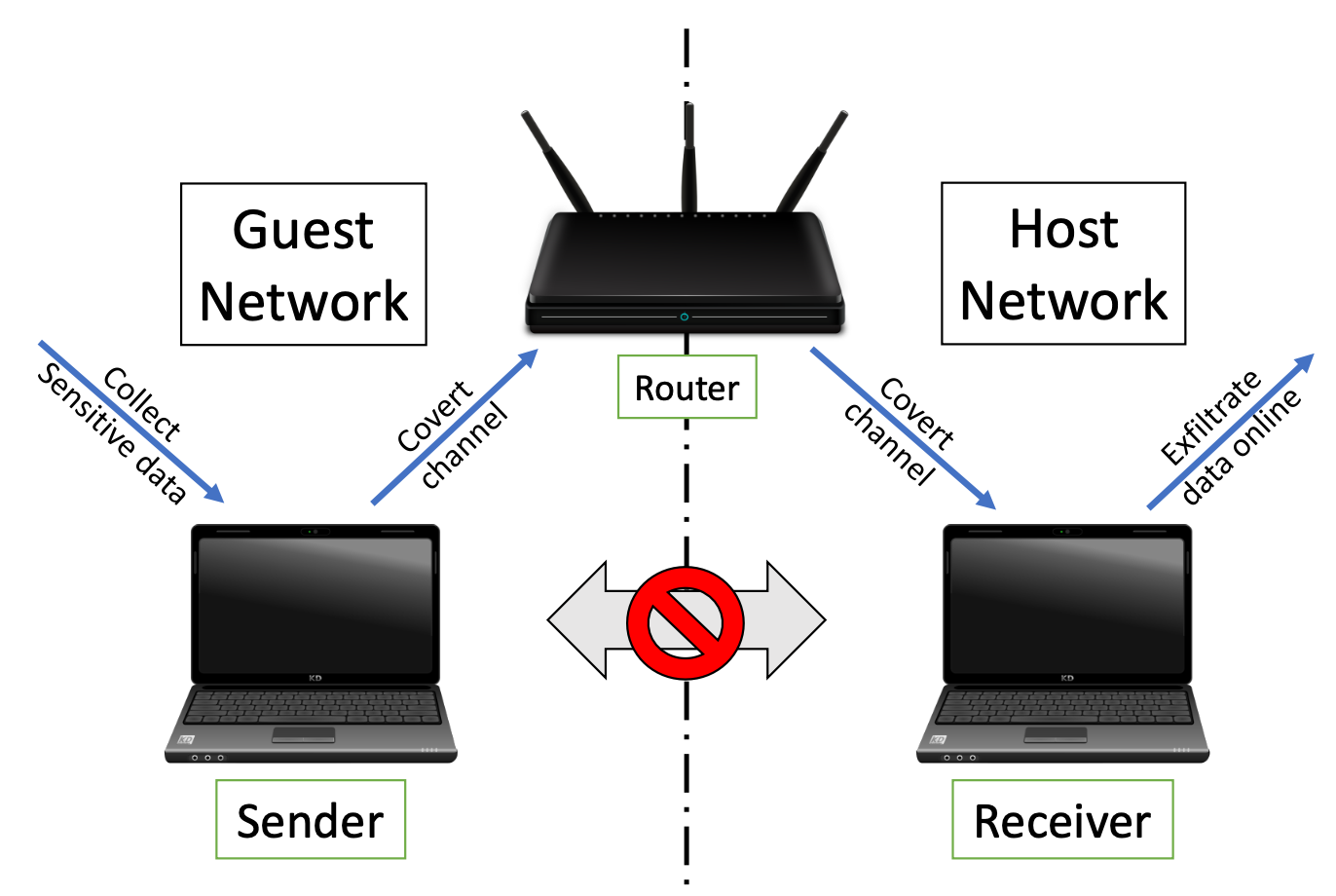
- Characterization and Detection of Cross-Router Covert Channels (Elsevier Computers & Security, January 2023, 103125)
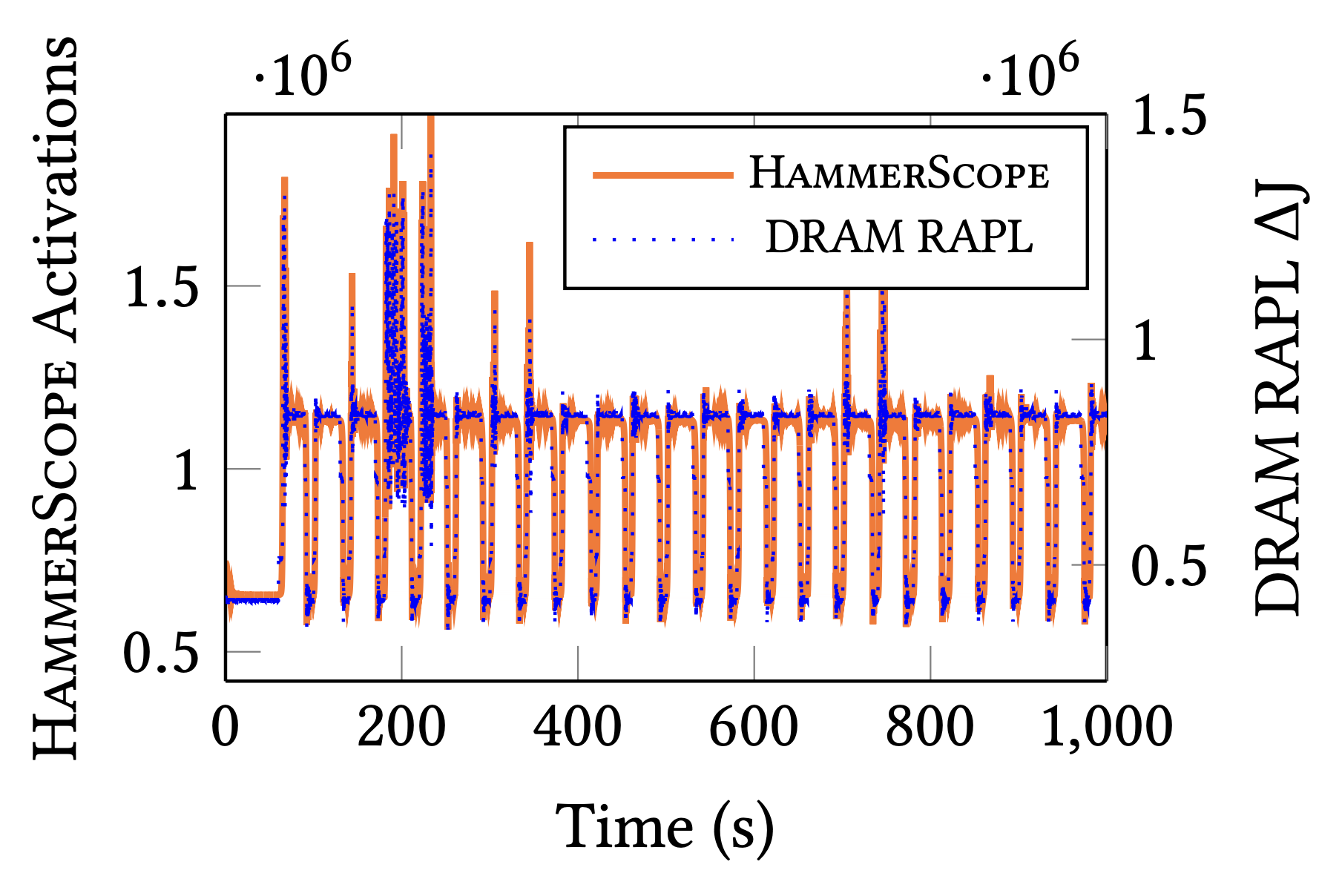
- HammerScope: Observing DRAM Power Consumption Using Rowhammer (29th ACM Conference on Computer and Communications Security (CCS), 2022)
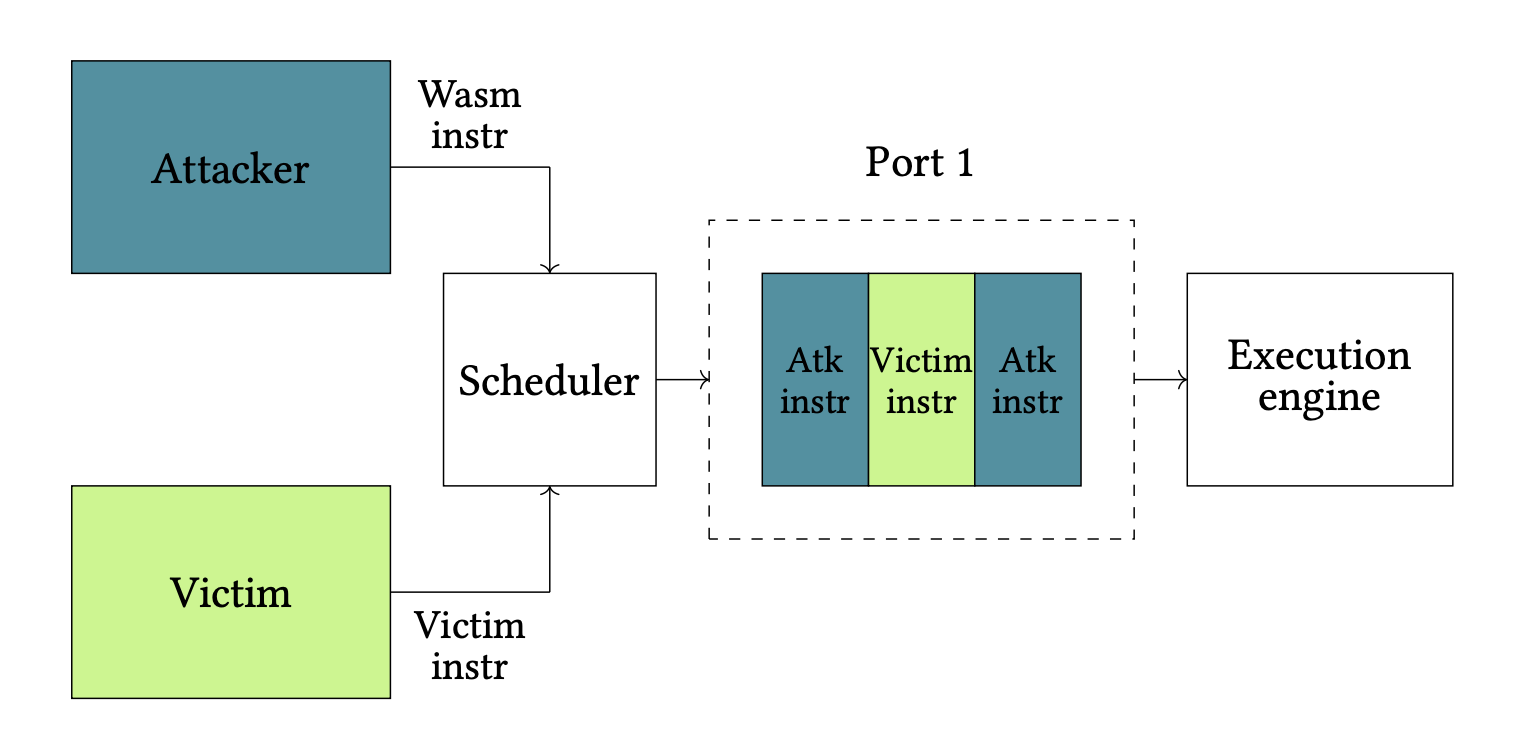
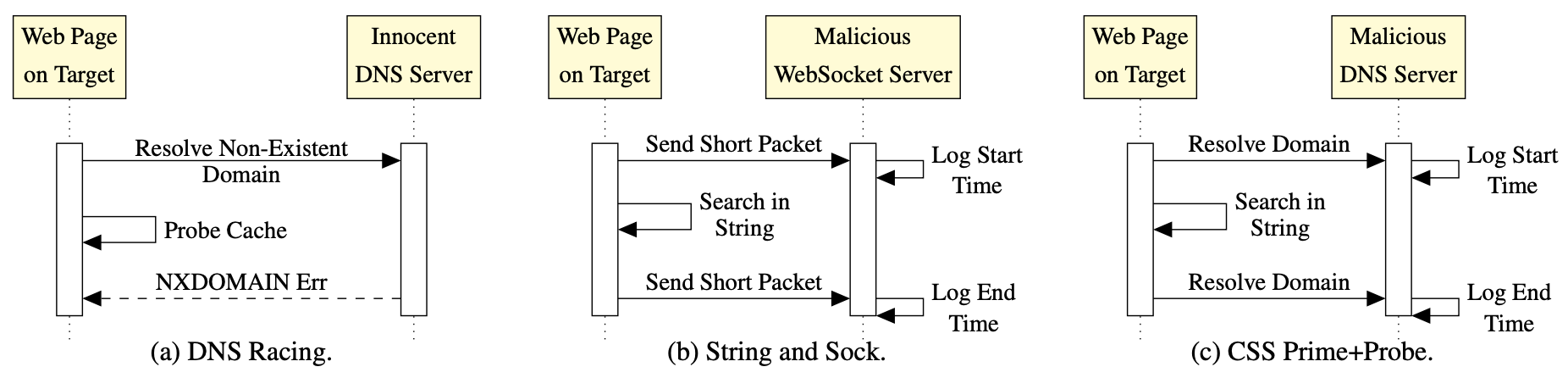
- Port Contention Goes Portable: Port Contention Side Channels in Web Browsers (17th ACM ASIA Conference on Computer and Communications Security, AsiaCCS 2022)
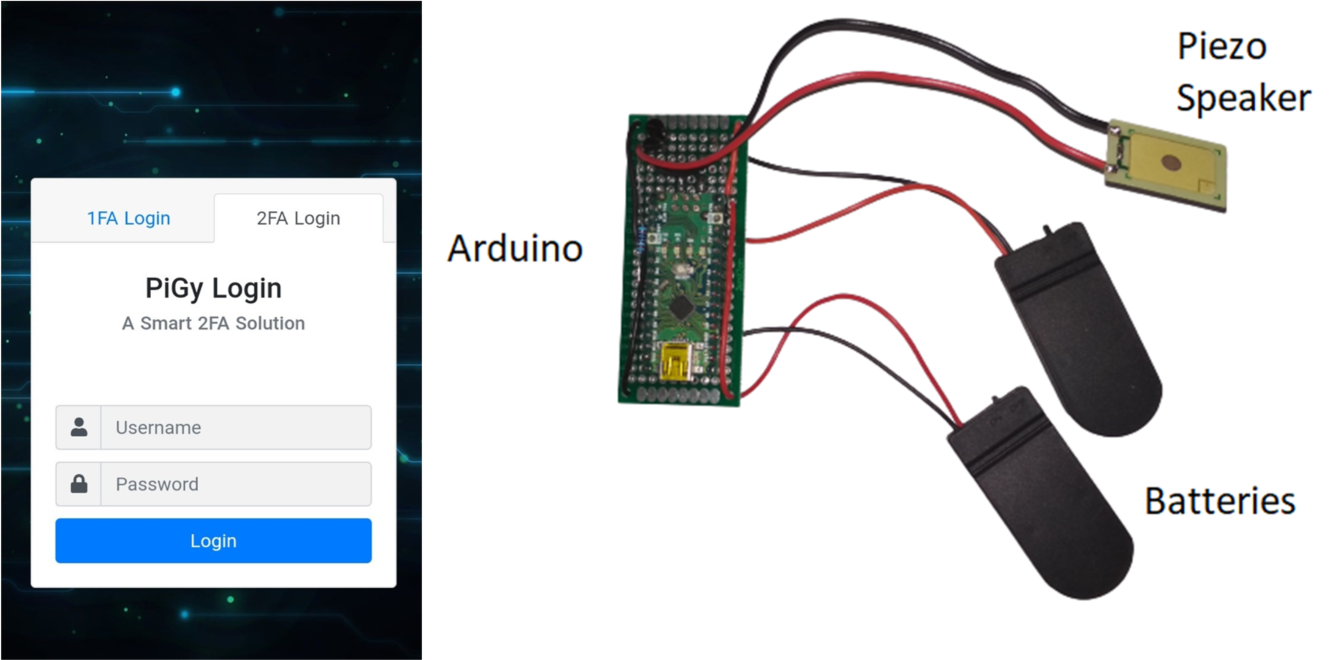
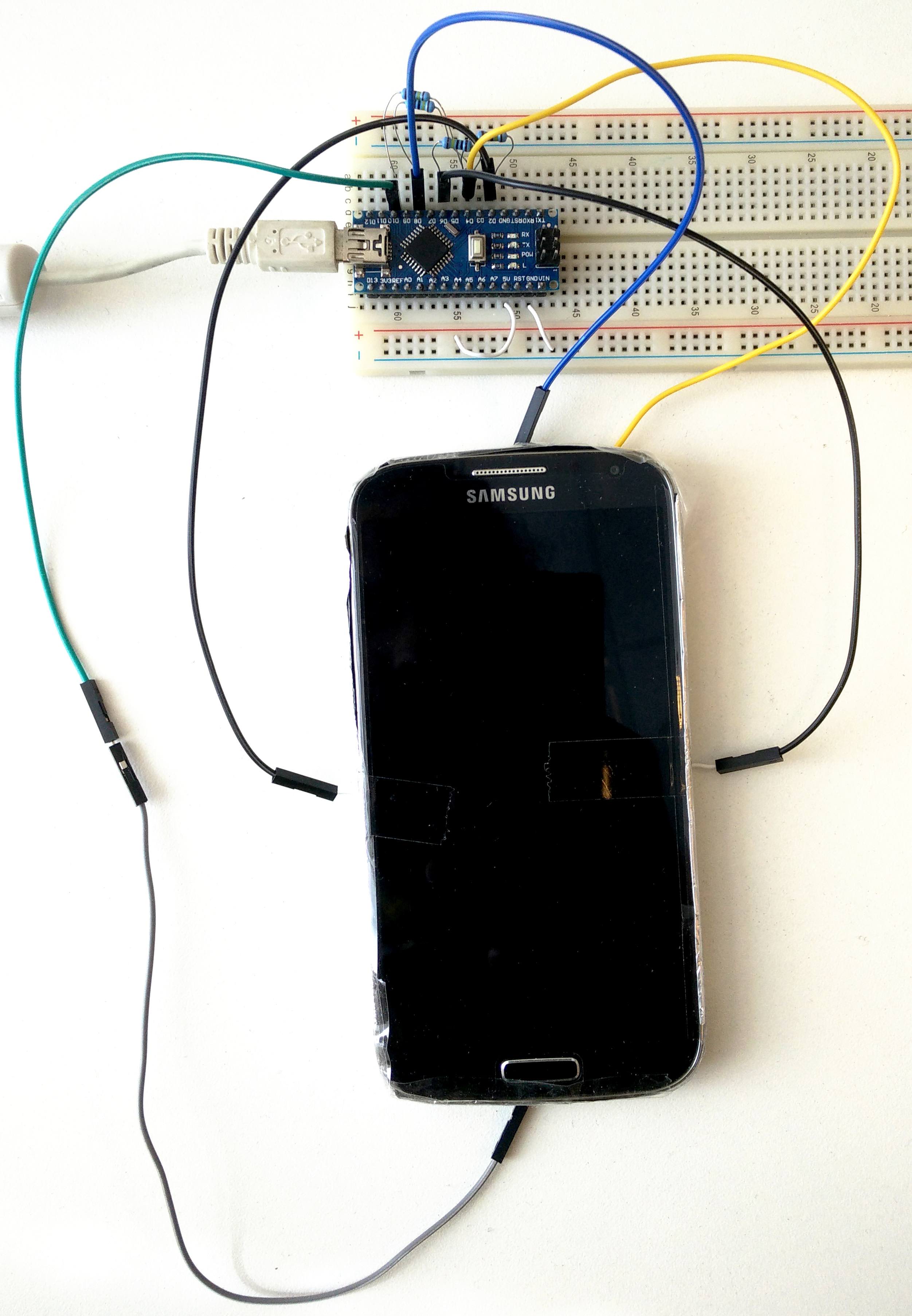
- Toward Usable and Accessible Two-Factor Authentication Based on the Piezo-Gyro Channel (IEEE Access, Volume 10, 2022)
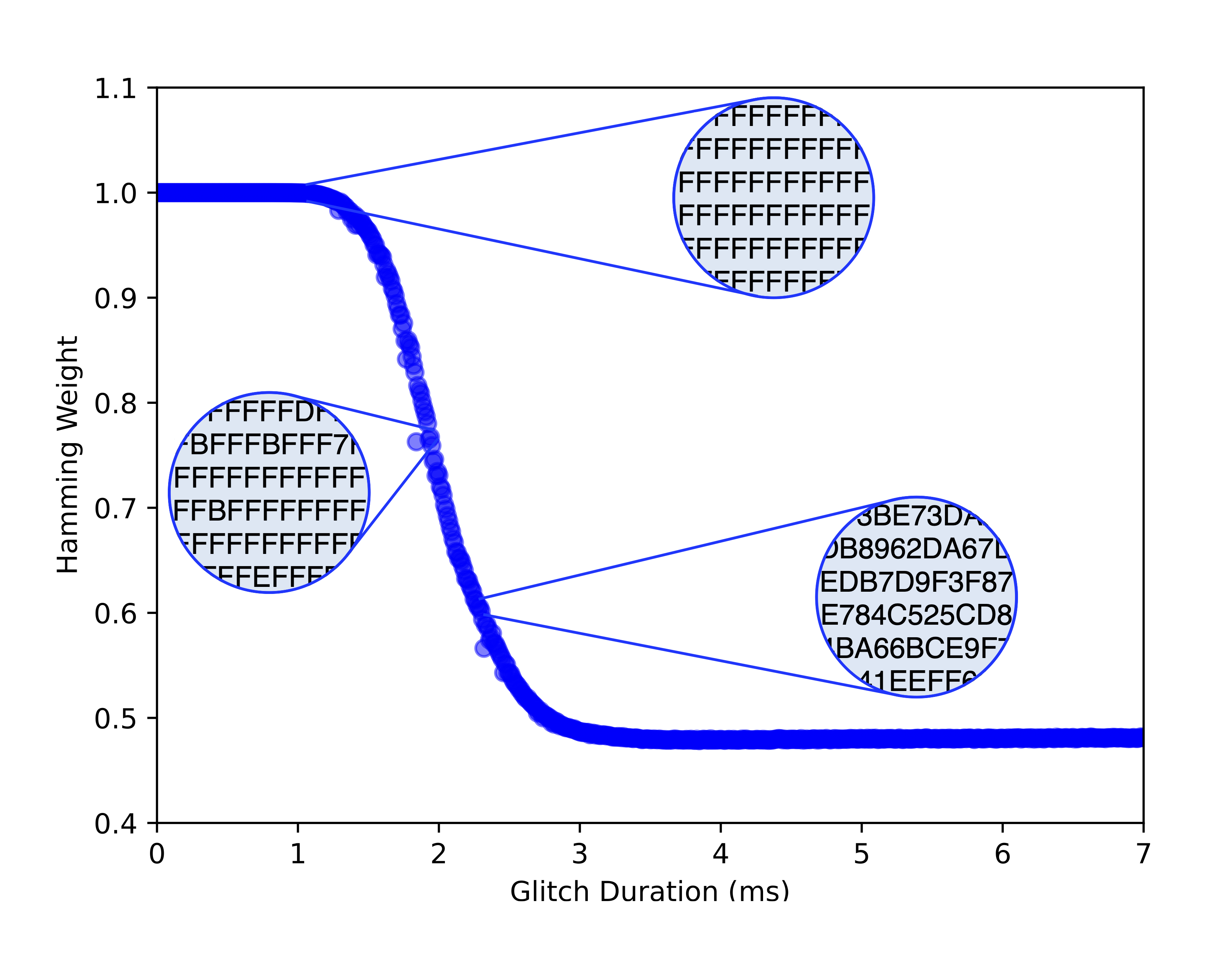
- Practical, Low-Cost Fault Injection Attacks on Personal Smart Devices (Applied Sciences, Volume 12 Issue 1, 2022)
- DRAWN APART : A Device Identification Technique based on Remote GPU Fingerprinting (29th Annual Network and Distributed System Security Symposium, NDSS 2022)
- Cache-based characterization: A low-infrastructure, distributed alternative to network-based traffic and application characterization (Elsevier Computer Networks Volume 200, December 2021)
- Website Fingerprinting Through the Cache Occupancy Channel and its Real World Practicality (IEEE Transactions on Dependable and Secure Computing Volume 18, Issue 5, September 2021)
- Prime+Probe 1, JavaScript 0: Overcoming Browser-based Side-Channel Defenses (30th USENIX Security Symposium, 2021)
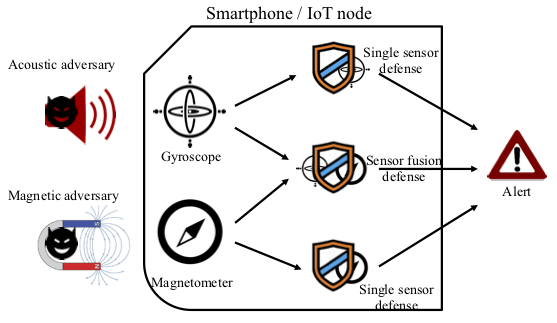
- Sensor Defense In-Software (SDI): Practical Defenses Against Spoofing Attacks on Position Sensors (Engineering Applications of Artificial Intelligence Volume 95, 2020)
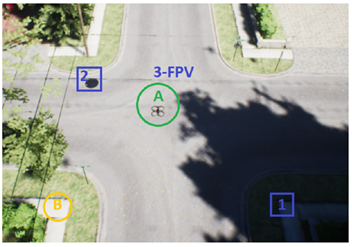
- Can the Operator of a Drone Be Located by Following the Drone’s Path? (4th International Symposium on Cyber Security Cryptography and Machine Learning, 2020)
- Cyber Security Threats in the Microbial Genomics Era: Implications for Public Health (Eurosurveillance Volume 25, Issue 6, 2020)
- Inner Conflict: How Smart Device Components Can Cause Harm (Elsevier Computers & Security, Volume 89, February 2020, 101665)
- Cross-Router Covert Channels (13th USENIX Workshop on Offensive Technologies (WOOT), 2019)
- Cyber Attack on SUUNTO Dive Computer (Technical Report)
- Robust Website Fingerprinting Through the Cache Occupancy Channel (28th USENIX Security Symposium, 2019)
- Reverse Engineering IoT Devices: Effective Techniques and Methods (IEEE Internet of Things Journal, Volume 5, Issue 6, 2019)
- Sensorless, Permissionless Information Exfiltration with Wi-Fi Micro-Jamming (12th USENIX Workshop on Offensive Technologies (WOOT), 2018)
- Brief Announcement: Deriving Context for Touch Events (Second International Symposium on Cyber Security Cryptography and Machine Learning (CSCML), 2018)
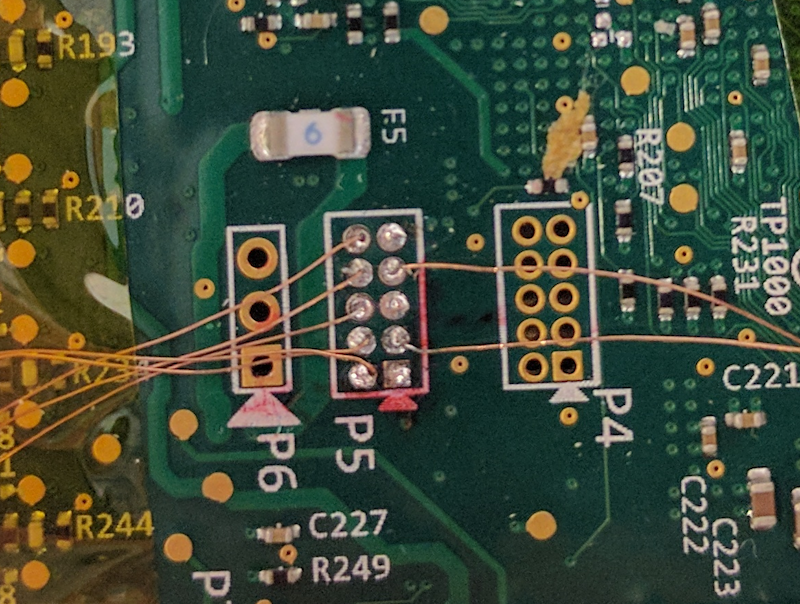
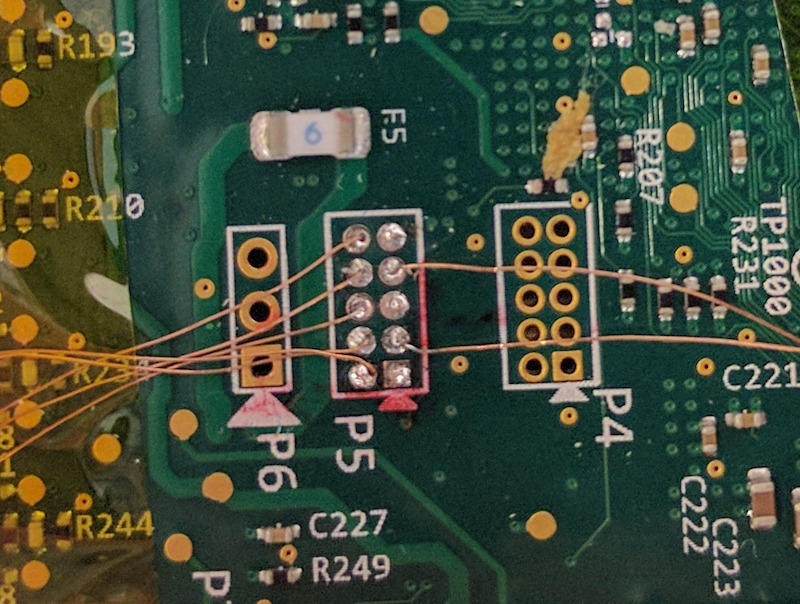
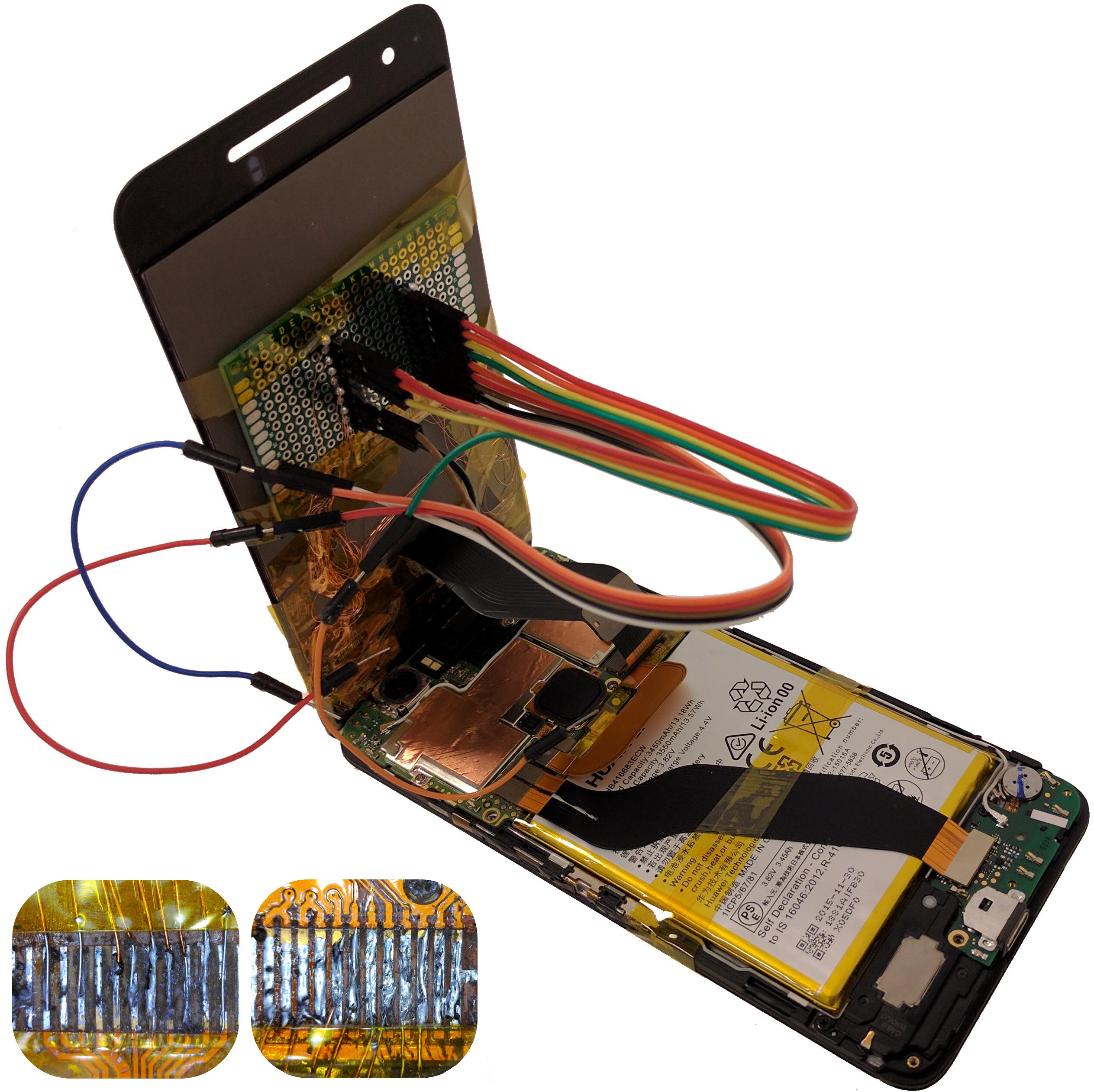
- Shattered Trust: When Replacement Smartphone Components Attack (11th USENIX Workshop on Offensive Technologies (WOOT), 2017)
- Opening Pandora's Box: Effective Techniques for Reverse Engineering IoT Devices (17th Smart Card Research and Advanced Application Conference (CARDIS), 2017)
- From Smashed Screens to Smashed Stacks: Attacking Mobile Phones Using Malicious Aftermarket Parts (Workshop on Security for Embedded and Mobile Systems (SEMS), 2017)
- The Curious Case of the Curious Case: Detecting touchscreen events using a smartphone protective case (Workshop on Security for Embedded and Mobile Systems (SEMS), 2017)
- How to Phone Home with Someone Else's Phone: Information Exfiltration Using Intentional Sound Noise on Gyroscopic Sensors (10th USENIX Workshop on Offensive Technologies (WOOT), 2016)
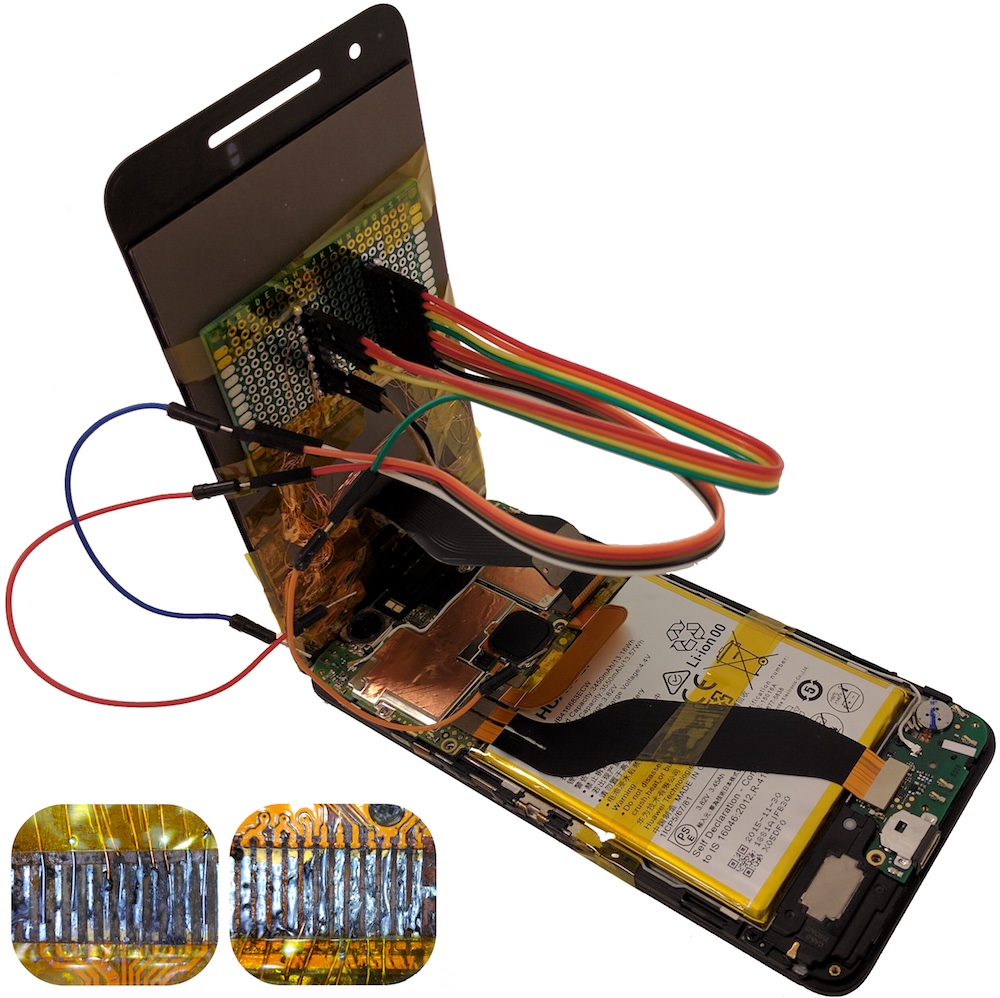
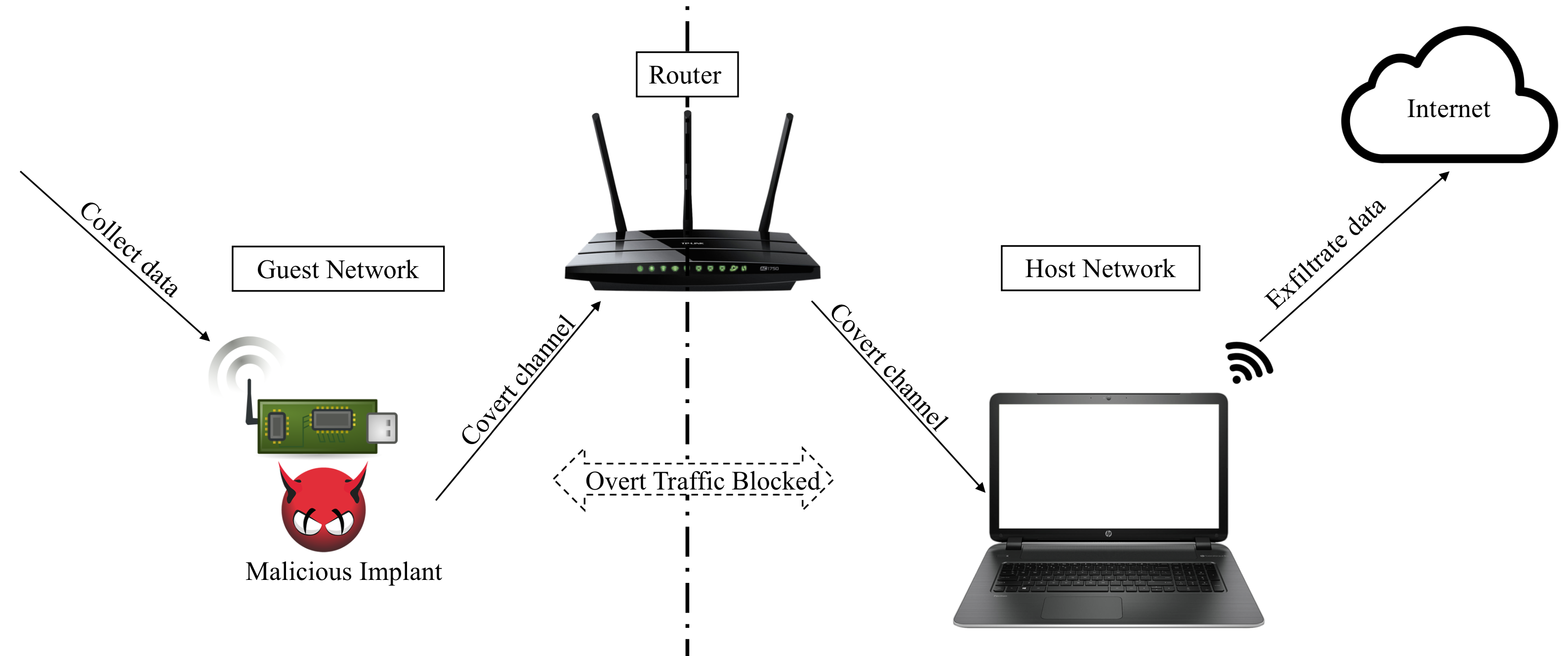
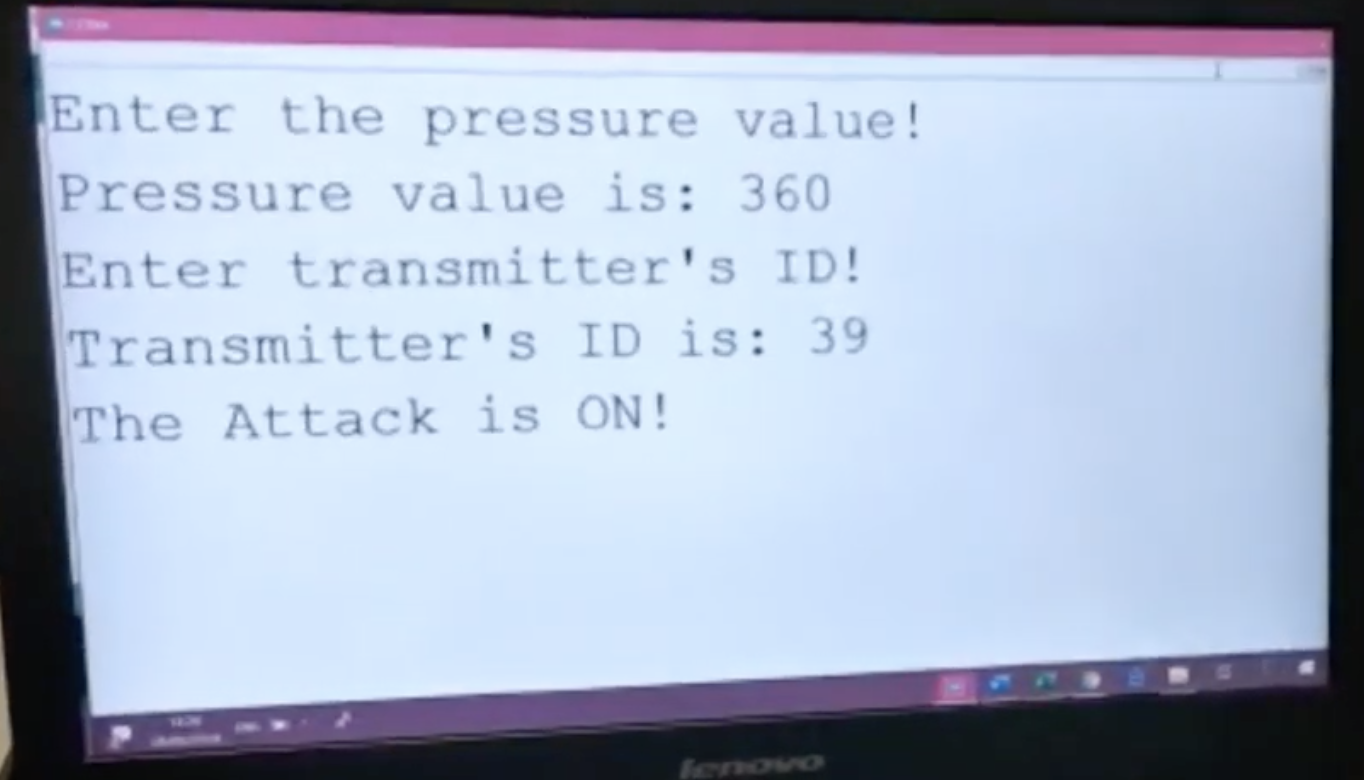
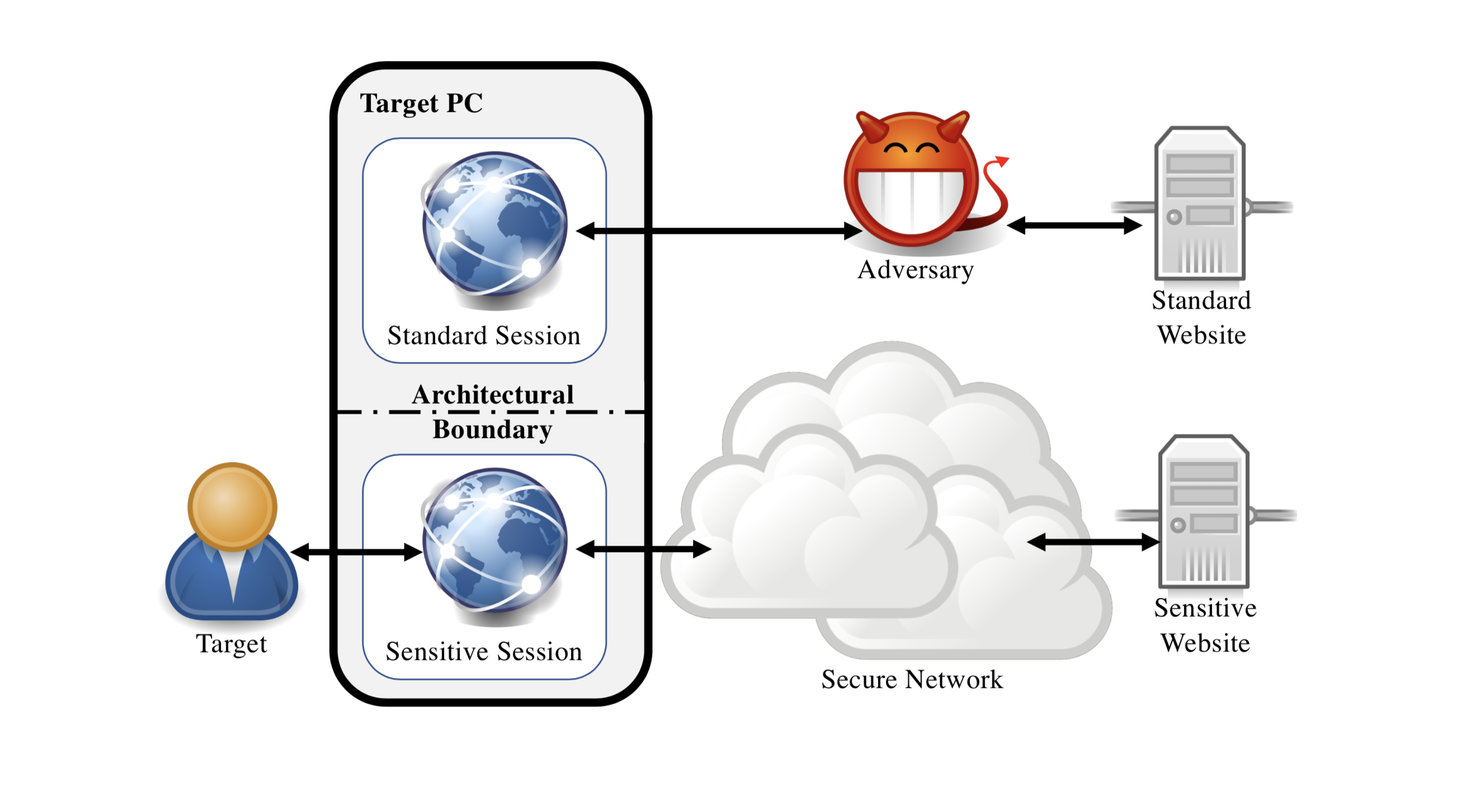


Prof. Yossi Oren is an Associate Professor in the Institute for Software, Systems and Security (S³) at the Stein Faculty of Computer and Information Science at Ben Gurion University of the Negev, and a member of BGU’s Cyber Security Research Center. Prior to joining BGU, Yossi was a Post-Doctoral Research Scientist in the Network Security Lab at Columbia University in the City of New York and a member of the security lab at Samsung Research Israel. He holds a Ph.D. in Electrical Engineering from Tel-Aviv University (thesis), and an M.Sc. in Computer Science from the Weizmann Institute of Science (thesis).
His research interests include implementation security (side-channel attacks, micro-architectural attacks, power analysis and other hardware attacks and countermeasures; low-resource cryptographic constructions for lightweight computers) and cryptography in the real world (consumer and voter privacy in the digital era; web application security). He has been recognized by The Register as a Top Boffin.
Personal homepage: https://iss.oy.ne.ro
Contact Information:
Building 96, Room 301
Department of Software and Information Systems Engineering
Faculty of Engineering Sciences
Ben-Gurion University of the Negev
P.O.B. 653
Beer-Sheva 8410501 Israel
Voice: +972 (74) 779-5122