Cross-Router Covert Channels
Authors: Adar Ovadya , Rom Ogen , Yakov Mallah , Niv Gilboa , Yossi Oren
Appeared in: 13th USENIX Workshop on Offensive Technologies (WOOT), 2019
Abstract
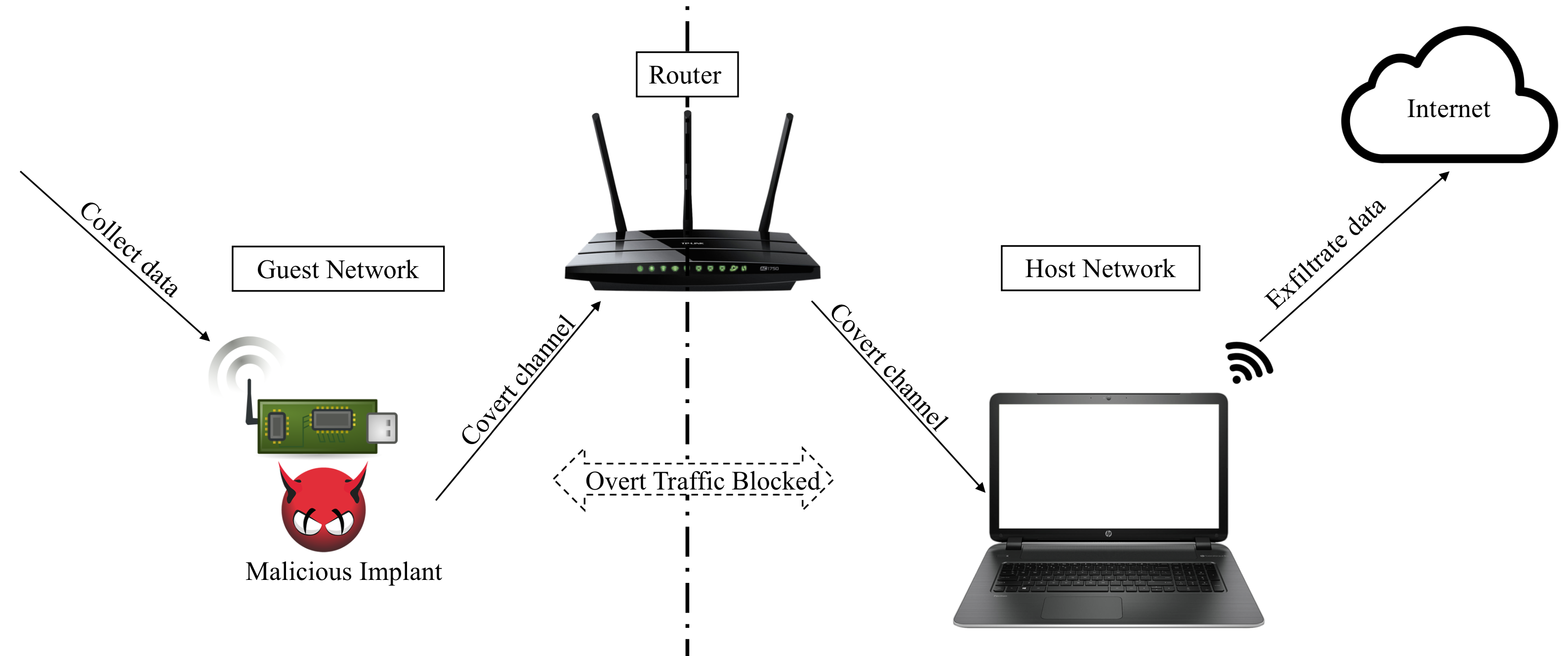
Many organizations protect secure networked devices from non-secure networked devices by assigning each class of devices to a different logical network. These two logical networks, commonly called the host network and the guest network, use the same router hardware, which is designed to isolate the two networks in software.
In this work we show that this isolation is ineffective in practice, by demonstrating the existence of cross-router covert channels. These channels allow leaking data between the host network and the guest network, and vice versa, through the use of the router as a shared medium. We performed a comprehensive survey of routers from multiple vendors and price points, and discovered that all of the routers we surveyed are vulnerable to at least one class of covert channel. Our attack can succeed even if the attacker has very limited permissions on the infected device, and even an iframe hosting malicious Javascript code can be used for this purpose. We provide several metrics for the effectiveness of such channels, based on their pervasiveness, rate and stealth, and discuss possible ways of identifying and preventing these cross-router leakages.