DRAWN APART : A Device Identification Technique based on Remote GPU Fingerprinting
Authors: Tomer Laor , Naif Mehanna , Vitaly Dyadyuk , Antonin Durey , Pierre Laperdrix , Clémentine Maurice , Yossi Oren , Romain Rouvoy , Walter Rudametkin , Yuval Yarom
Appeared in: 29th Annual Network and Distributed System Security Symposium, NDSS 2022
Abstract
Browser fingerprinting aims to identify users, or their devices, from scripts that execute in the users’ browser and collect specific information on the software or hardware characteristics. Fingerprinting is used in practice on the Internet to track users, or as an additional means of identification to improve security. These fingerprinting techniques have one significant limitation: they are unable to track individual users for an extended duration. This happens because the fingerprint tends to evolve over time, and these evolutions ultimately cause the fingerprint to be confused with fingerprints from other devices with similar hardware and software.
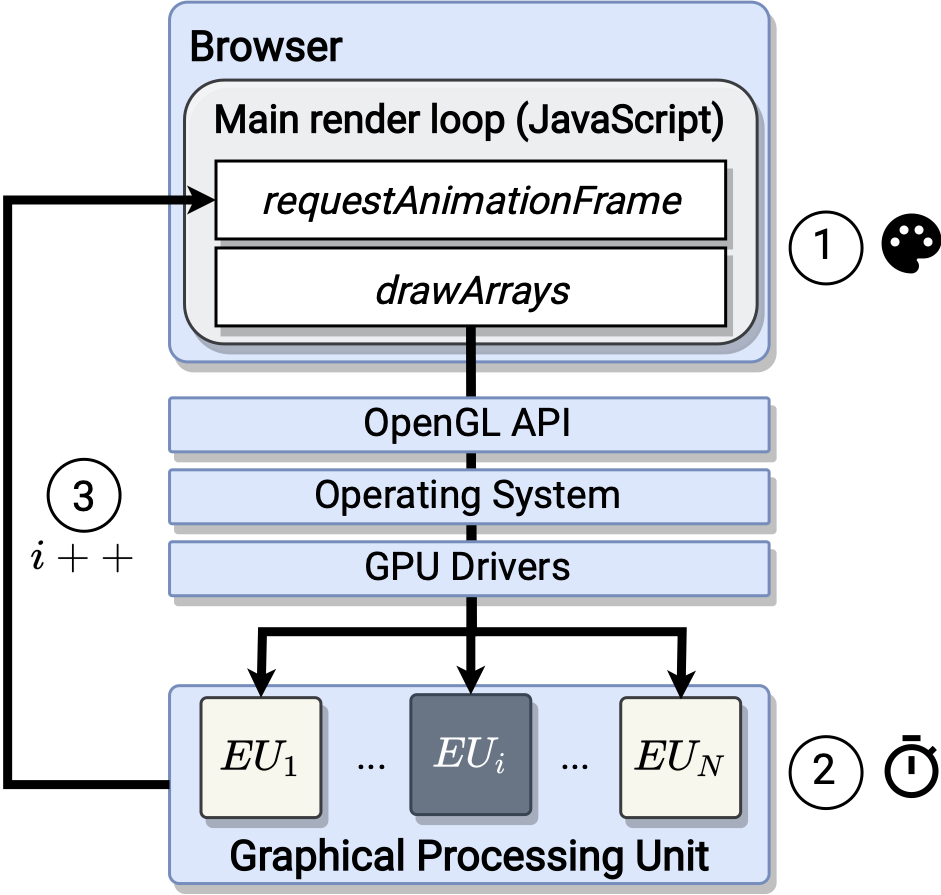
In this paper, we report on a new technique, which can significantly extend the tracking time of fingerprint-based tracking methods. Our technique, which we call DrawnApart, is a new GPU fingerprinting technique that identifies a device from the unique properties of its GPU stack. Specifically, we show that variations in speed among the multiple execution units that comprise a GPU can serve as a reliable and robust device signature, which can be collected using unprivileged JavaScript.
We investigate the accuracy of DrawnApart under two different scenarios. In the first scenario, our controlled experiments confirm that the technique is effective in telling apart devices with similar hardware and software configurations, even when they are considered identical by current state-of-the-art fingerprinting algorithms. In the second scenario, we create and integrate a one-shot learning version of our technique in the browser fingerprinting state-of-the-art Internet-wide tracking algorithm. Verifying our technique through a large-scale experiment involving data collected from over 2,500 crowd-sourced devices over a period of several months, we show how our technique provides up to a 67% boost to the median tracking duration of the algorithm, compared to the state-of-the-art method.
DrawnApart makes two contributions to the state of the art in browser fingerprinting. On the conceptual front, it is the first work that looks at manufacturing differences between identical GPUs and the first to exploit these differences in a privacy context. On the practical front, it demonstrates a robust technique for distinguishing between machines with identical hardware and software configurations, a technique that delivers practical accuracy gains in a realistic setting.
Explanation of the paper on the AmIUnique Blog
Artifacts are available online