Characterization and Detection of Cross-Router Covert Channels
Authors: Oren Shvartzman , Adar Ovadya , Kfir Zvi , Omer Shwartz , Rom Ogen , Yakov Mallah , Niv Gilboa , Yossi Oren
Appeared in: Elsevier Computers & Security, January 2023, 103125
Abstract
In covert channel attacks, an adversary seeks various means to influence a tangible characteristic of a system, and then makes the systems leak information by measuring this characteristic. Covert channels are, by nature, very elusive. This makes it very difficult to identify them and defend against attacks that use these channels to leak sensitive information. Thus, they are a serious threat to the security of many systems.
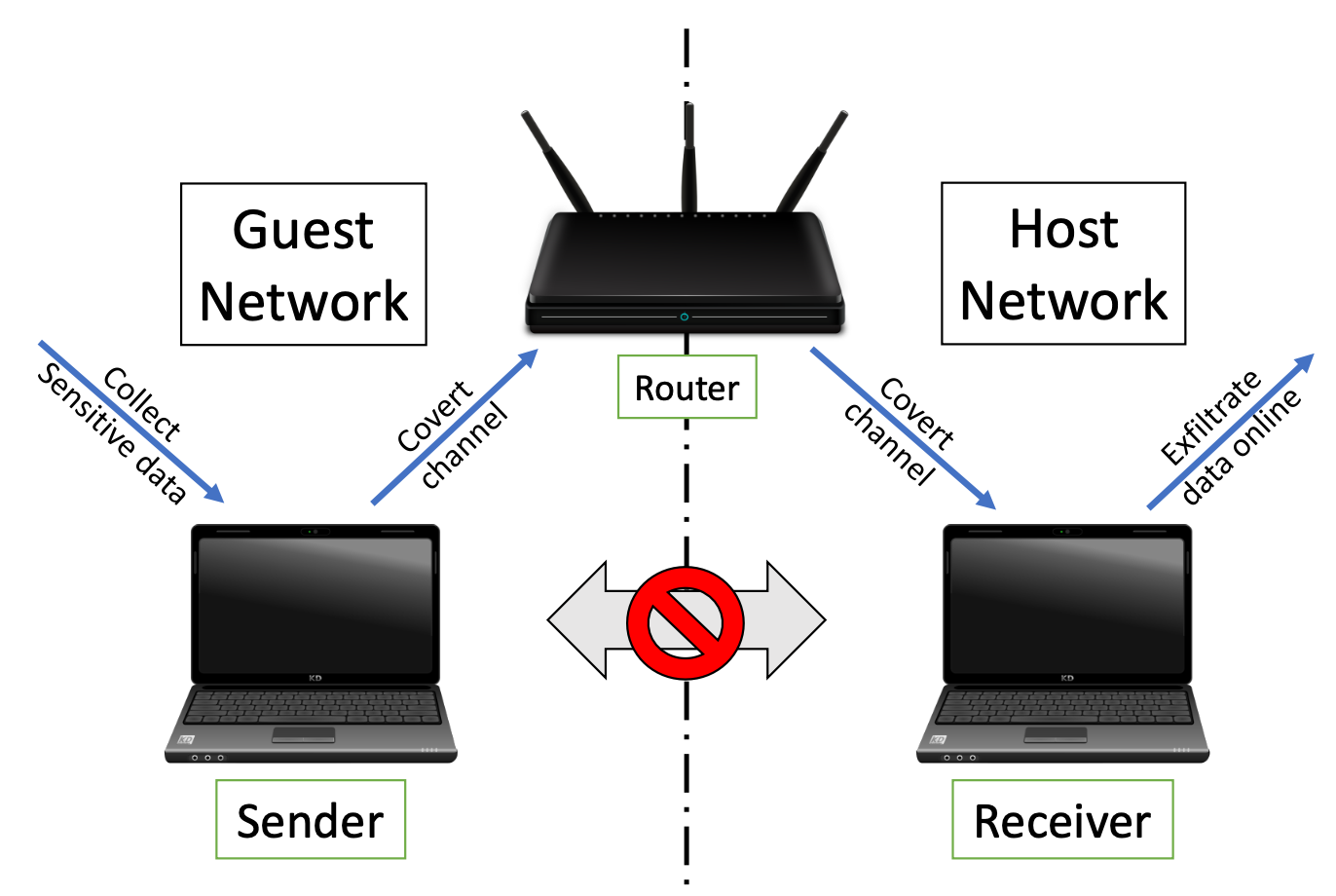
In this paper, we present two network timing covert channel attacks, and a defense mechanism against them. The purpose of the proposed attacks is to leak sensitive information between two logically separated (or isolated) networks that are hosted by a single router – one that is connected to the Internet, and another that is isolated and contains sensitive information. The attacks build on the fact that the response time of the router for a specific type of packet sent from a device that is connected to it is usually predictable, given the network topology. By interacting with the single shared router in a specific manner, an attacker can increase the router’s packet response time. The interaction is determined based on the information to be leaked, so the receiver (a computer located on the Internet-connected network) can measure the delayed packet response times and decode the sender’s signals (which operates from the isolated network) to receive classified information. The two classes of attacks presented in this work differ in the way that the delay is caused. In the cross-router covert channel (CRCC) attack, the sender overloads the router with control-plane packets; in the Wi-Fi micro-jamming attack, the sender uses a pre-installed implant to transmit single-tone signals in the 2.4GHz frequency range, disturbing the router’s packet transmissions. We showed that both attacks can influence a wide range of router brands and Wi-Fi capable devices and evaluated the optimal settings for both attacks when using different types of packets, transmission power, and data transmission rates.
Our proposed defense mechanism is based on semi-supervised machine learning and deep learning algorithms, which are both used for novelty detection in network traffic. By detecting unusual traffic, we can identify the disturbances needed to leak the information. The system can then respond by blocking the suspicious devices that are involved in the attack. We evaluated the attacks in noisy and noise-free environments, successfully detecting both attacks in both environments. All the data and code, which includes the implementation of the attacks and the defense mechanism, is published as a benefit to the research community.
Artifact Availability: All the code and data used in this work can be found in the online artifact repository