Prime+Probe 1, JavaScript 0: Overcoming Browser-based Side-Channel Defenses
Authors: Anatoly Shusterman , Ayush Agarwal , Sioli O’Connell , Daniel Genkin , Yossi Oren , Yuval Yarom
Appeared in: 30th USENIX Security Symposium, 2021
Abstract
The “eternal war in cache” has reached browsers, with multiple cache-based side-channel attacks and countermeasures being suggested. A common approach for countermeasures is to disable or restrict JavaScript features deemed essential for carrying out attacks.
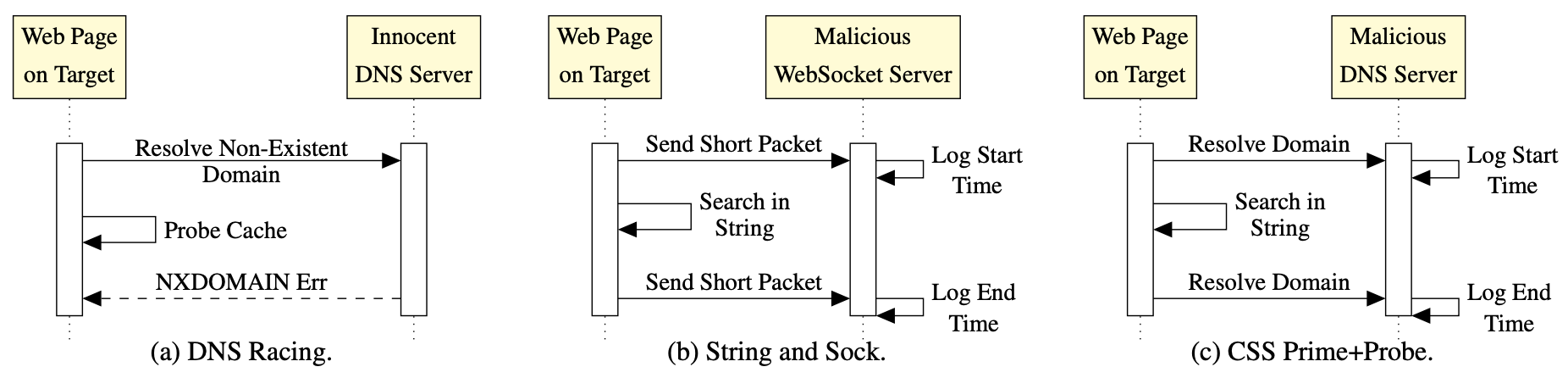
To assess the effectiveness of this approach, in this work we seek to identify those JavaScript features which are essential for carrying out a cache-based attack. We develop a sequence of attacks with progressively decreasing dependency on JavaScript features, culminating in the first browser- based side-channel attack which is constructed entirely from Cascading Style Sheets (CSS) and HTML, and works even when script execution is completely blocked. We then show that avoiding JavaScript features makes our techniques architecturally agnostic, resulting in microarchitectural website fingerprinting attacks that work across hardware platforms including Intel Core, AMD Ryzen, Samsung Exynos, and Apple M1 architectures.
As a final contribution, we evaluate our techniques in hardened browser environments including the Tor browser, DeterFox (Cao el al., CCS 2017), and Chrome Zero (Schwartz et al., NDSS 2018). We confirm that none of these approaches completely defend against our attacks. We further argue that the protections of Chrome Zero need to be more comprehensively applied, and that the performance and user experience of Chrome Zero will be severely degraded if this approach is taken.
Extended version now available!
What is the Prime + Probe Attack?
The Prime + Probe Attack is a type of side-channel attack used to recover secrets from systems with shared cache memory. It was invented in 2005 by a trio of researchers: Dag Arne Osvik, Adi Shamir, and Eran Tromer.
For a more detailed explanation of the attack and its implications, please check out this video by Yuval Yarom, or this video by Yossi Oren and its associated lecture notes.
Video (ESORICS Tutorial)
Press Coverage
- SecurityWeek
- The 8-Bit
- 9to5Mac
- AppleInsider
- Hacker.ru (in Russian)
- The Hacker News
- The Record
- cnBeta (in Chinese)
- MacGeneration (in French)
- Reddit and 4Chan
Artifact Repository
Our artifact repository, which contains demo attack pages for Cache Contention, Count Sweeps, String and Sock, and CSS PP0, as well as a Python notebook showing classification over real data, can be found at the following link.