Sensor Defense In-Software (SDI): Practical Defenses Against Spoofing Attacks on Position Sensors
Authors: Kevin Sam Tharayil , Benyamin Farshteindiker , Shaked Eyal , Nir Hasidim , Roy Hershkovitz , Shani Houri , Ilia Yoffe (Iofedov) , Michal Oren , Yossi Oren
Appeared in: Engineering Applications of Artificial Intelligence Volume 95, 2020
Abstract
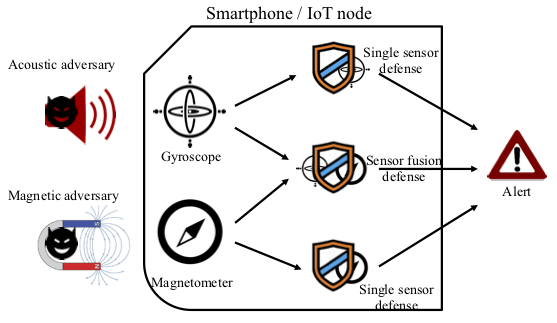
Position sensors, such as the gyroscope, the magnetometer and the accelerometer, are found in a staggering variety of devices, from smartphones and UAVs to autonomous robots. Several works have shown how adversaries can mount spoofing attacks to remotely corrupt or even completely control the outputs of these sensors. With more and more critical applications relying on sensor readings to make important decisions, defending sensors from these attacks is of prime importance.
In this work we present practical software based defenses against attacks on two common types of position sensors, specifically the gyroscope and the magnetometer. We first characterize the sensitivity of these sensors to acoustic and magnetic adversaries. Next, we present two software-only defenses: a machine learning based single sensor defense, and a sensor fusion defense which makes use of the mathematical relationship between the two sensors. We performed a detailed theoretical analysis of our defenses, and implemented them on a variety of smartphones, as well as on a resource-constrained IoT sensor node. Our defenses do not require any hardware or OS-level modifications, making it possible to use them with existing hardware. Moreover, they provide a high detection accuracy, a short detection time and a reasonable power consumption.
An early version of this manuscript was published on ArXiv as arXiv cs.CR 1905.04691, 2019.