The Attack Surface of Wet Lab Automation
Authors: Naor Dalal , Yossi Oren , Yuval Dorfan , Jonathan Giron , Rami Puzis
Appeared in: Cyberbiosecurity
Abstract
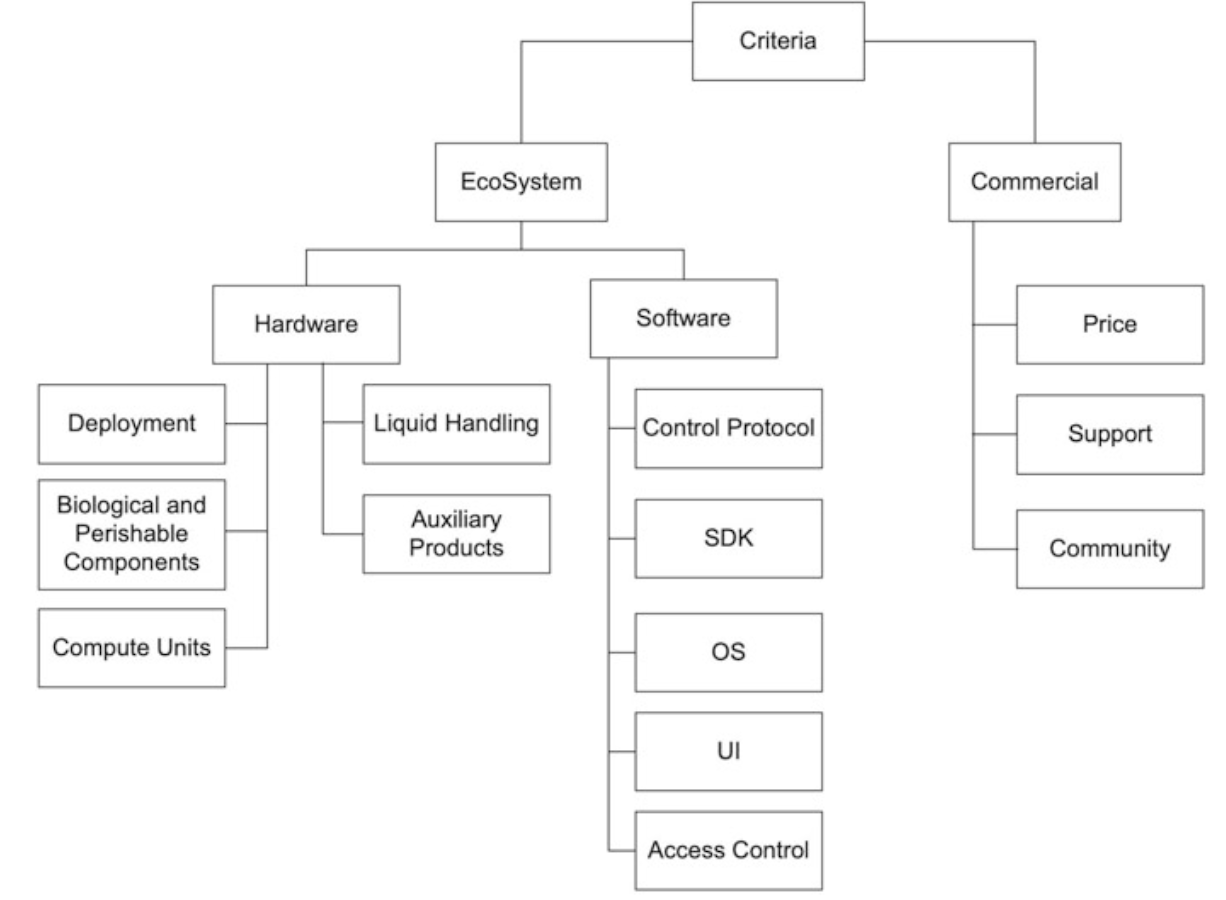
Robotic liquid handlers save human effort and are, in many cases, faster and more precise than a human operator. They can be operated and controlled remotely and do not require technical programming skills from their operators. Unfortunately, like many other high-tech products, robotic wet lab automation may have exploitable vulnerabilities and design weaknesses that allow subversion by an adversary. The distributed nature and remote control capabilities of wet lab automation expand its attack surface increasing the opportunities for an attack to interfere with the executed biological protocols, affect medical products, and alter test results. Perimeter defenses are known to be insufficient for proper protection of systems. Security needs to be considered throughout the entire pipeline of wet lab operations, including machinery, local- and cloud-based software, and even biological protocols. In this chapter, we review the most prominent types of robots in a biological laboratory through the lens of cyber-biosecurity and map the general attack surface of wet lab automation.