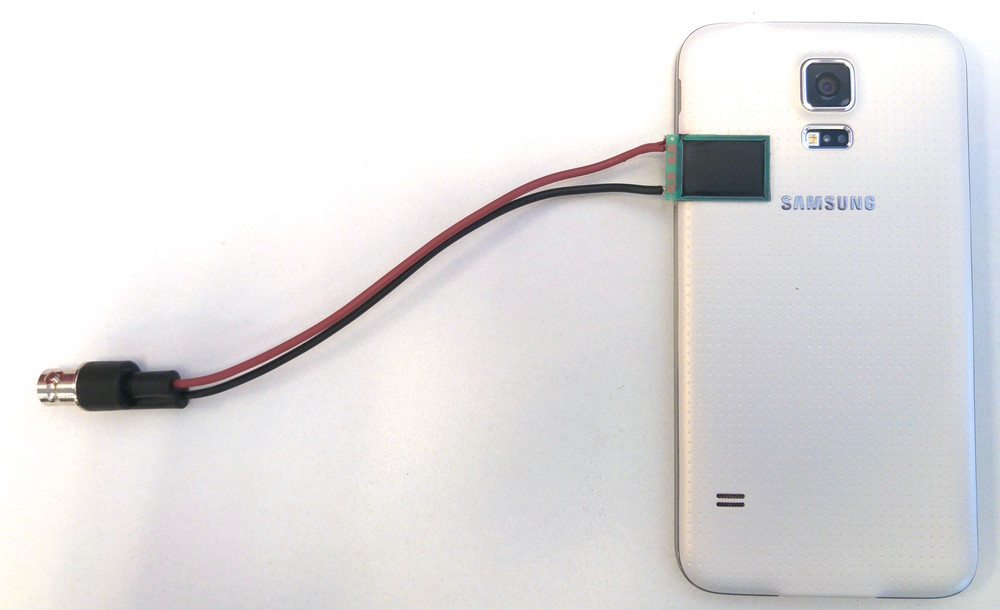
Publications
Engineering Sensor Spoofing Protection into the Android Operating System
Authors: Roy Hershkovitz, Yossi Oren
Appeared in: IEEE Access (early access)
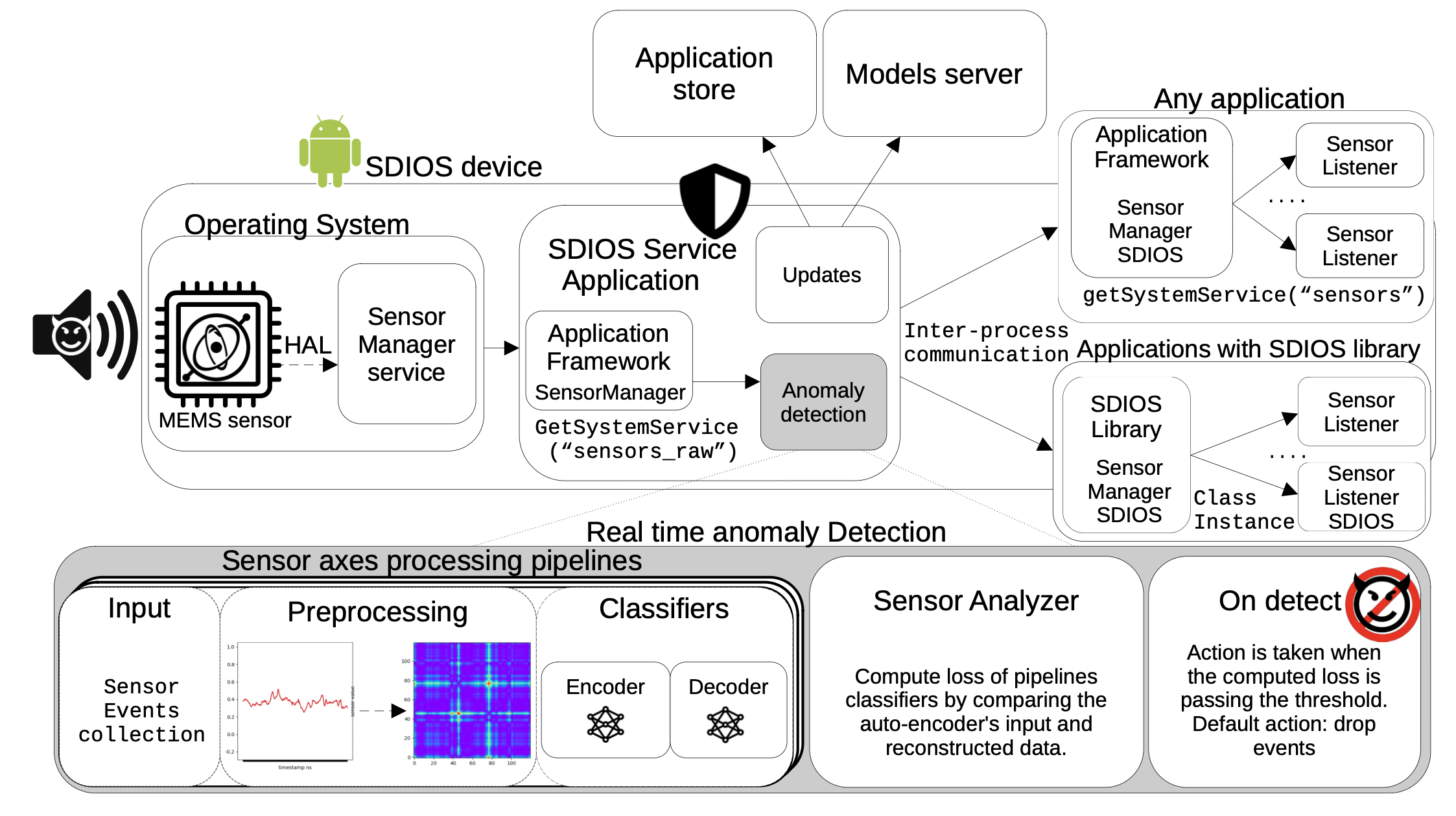
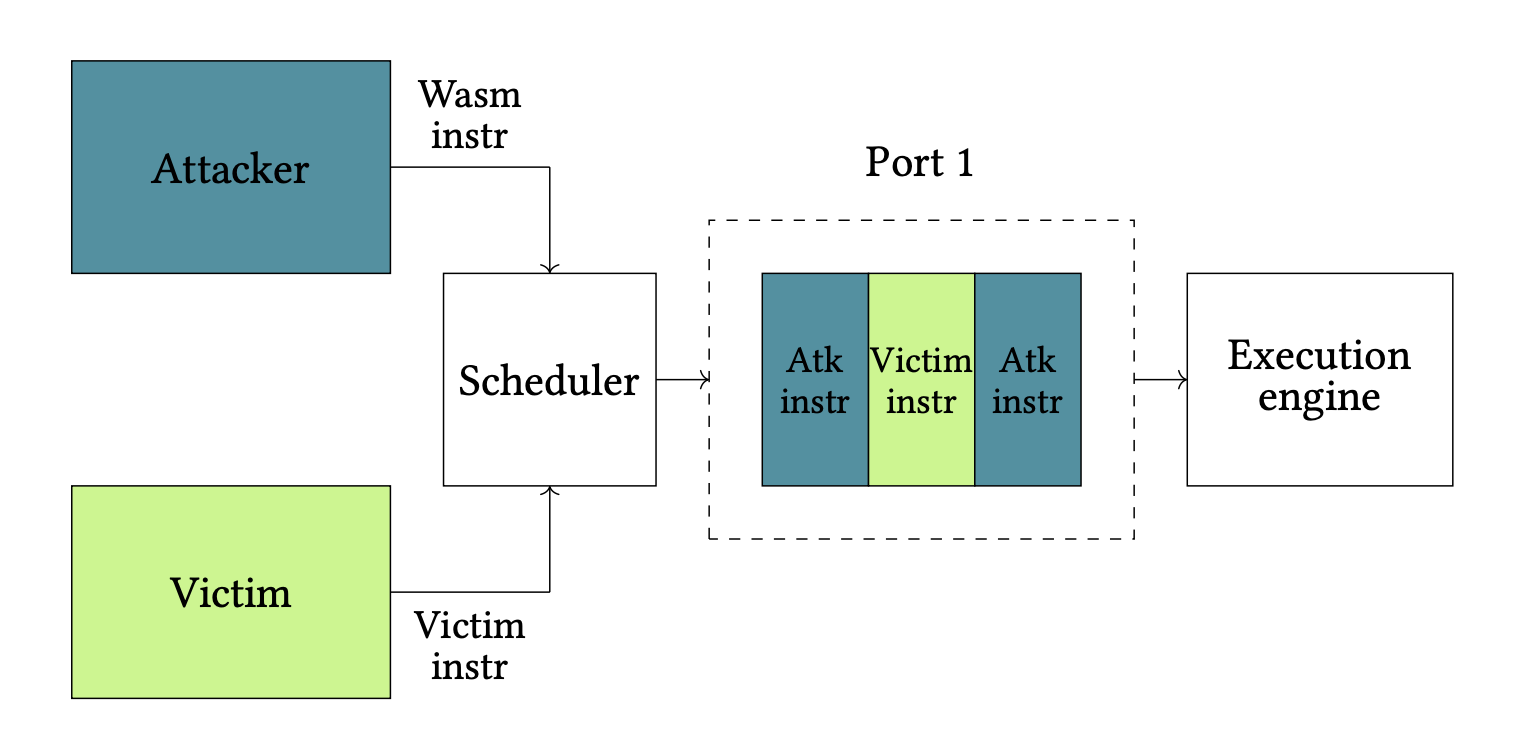
A Second Look at Port Assignment on Intel CPUs (work in progress)
Authors: Yarin Oziel, Tomer Laor, Shlomi Levy, Clémentine Maurice, Yossi Oren, Thomas Rokicki, Gabriel Scalosub
Appeared in: 2nd Microarchitecture Security Conference, 2026
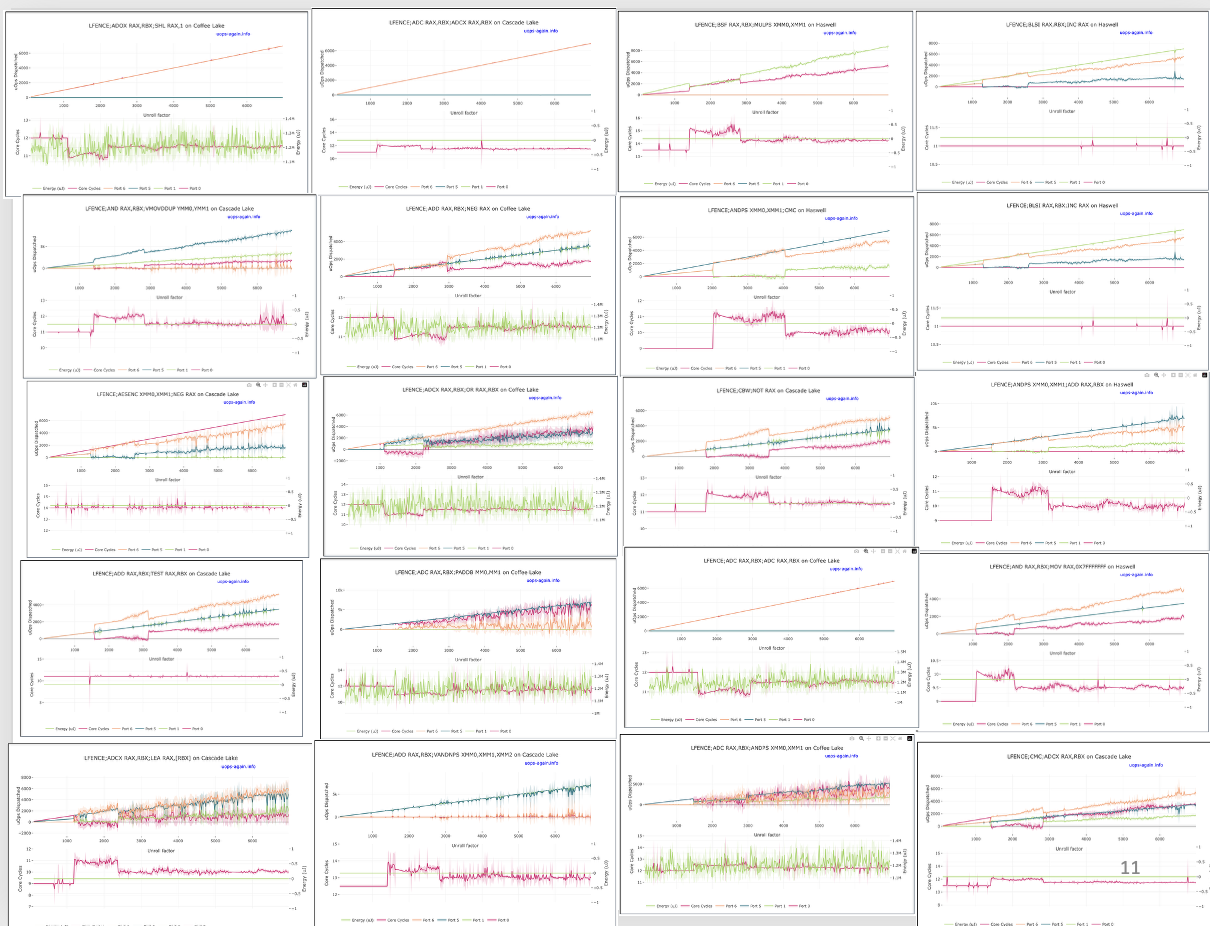
Understanding and Addressing Concept Drift in Website Fingerprinting
Authors: Roie David, Anatoly Shusterman, Yossi Oren
Appeared in: Elsevier Computer Networks Journal, to appear
IRIS: Enhancing the Security of IoT Devices Using Internal IR-Based Sensors
Authors: Amit Kama, Yarin Kalfon, Yossi Oren
Appeared in: Elsevier Internet of Things Journal, Volume 34, November 2025, 101787
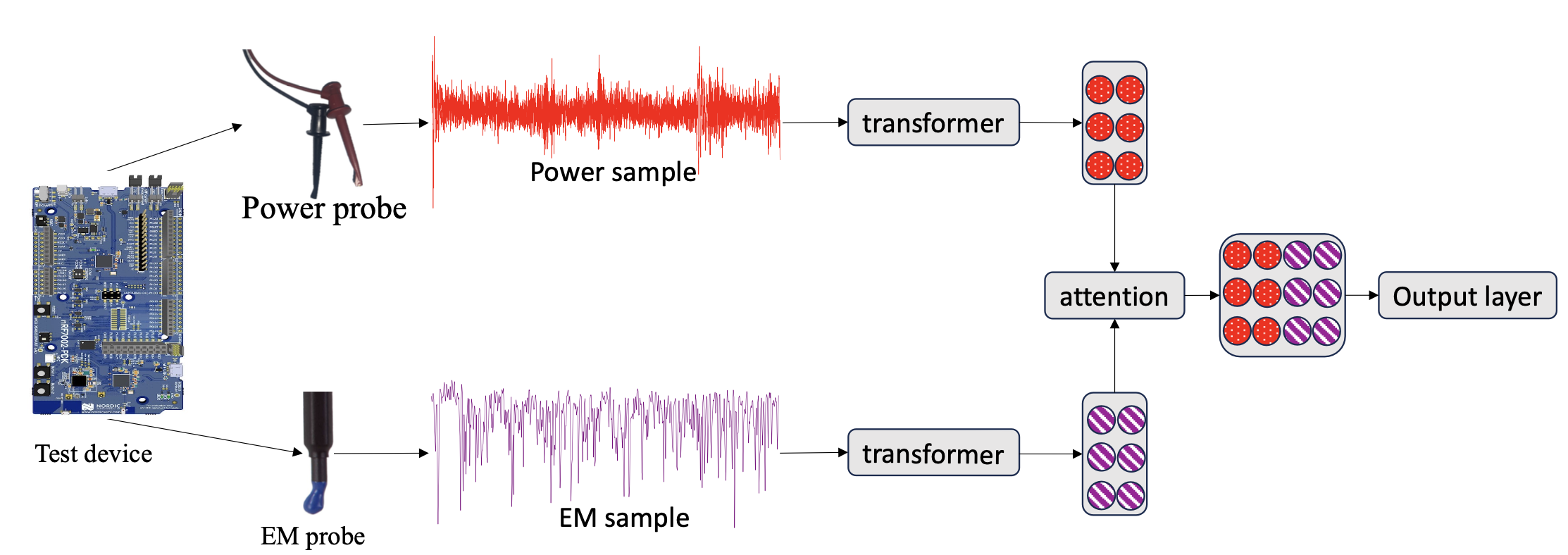
Two's Complement: Monitoring Software Control Flow using Both Power and Electromagnetic Side Channels
Authors: Michael Amar, Lojenaa Navanesan, Asanka P. Sayakkara, Yossi Oren
Appeared in: 27th Euromicro Conference on Digital System Design, 2024
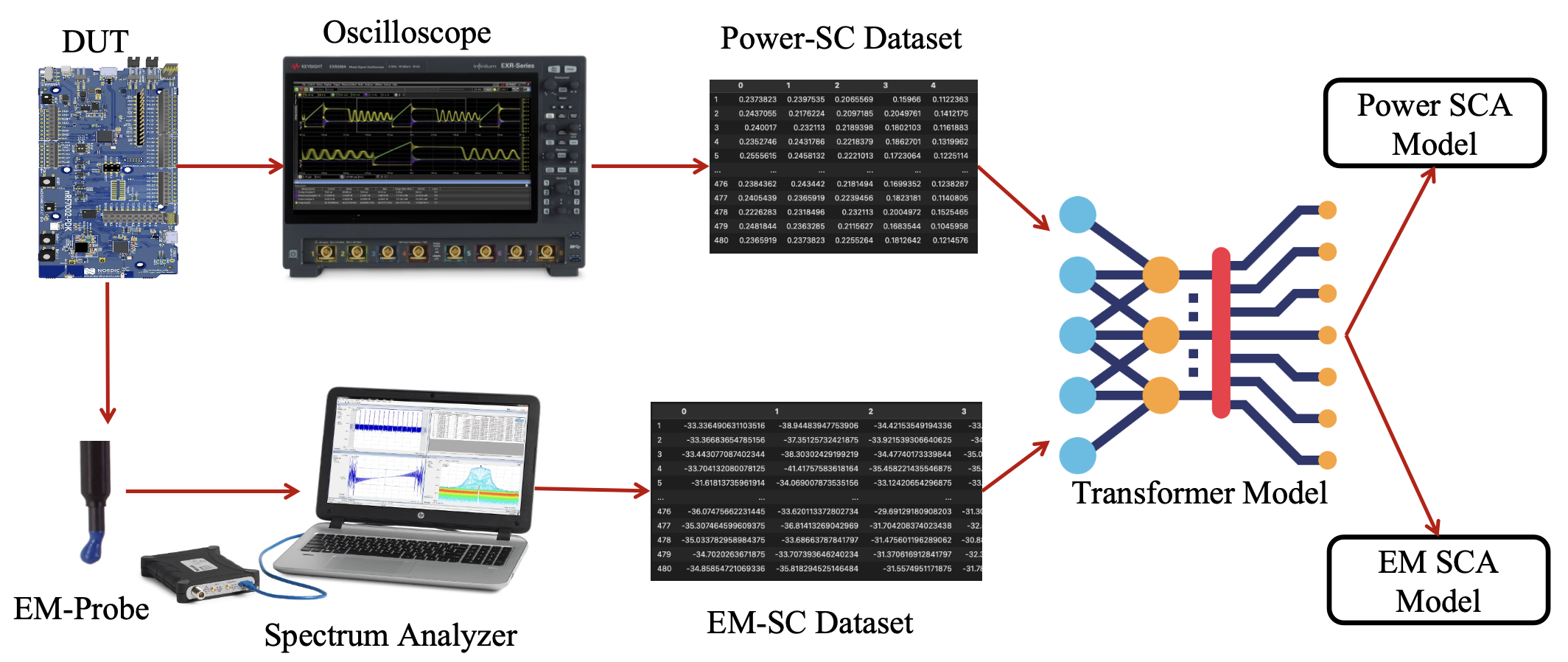
Waves of Knowledge: A Comparative Study of Electromagnetic and Power Side-Channel Monitoring in Embedded Systems
Authors: Michael Amar, Lojenaa Navanesan, Asanka P. Sayakkara, Yossi Oren
Appeared in: EAI SmartSP 2023
Pixel Thief: Exploiting SVG Filter Leakage in Firefox and Chrome
Authors: Sioli O'Connell, Lishay Aben Sour, Ron Magen, Daniel Genkin, Yossi Oren, Hovav Shacham, Yuval Yarom
Appeared in: 33rd USENIX Security Symposium, 2024
The Attack Surface of Wet Lab Automation
Authors: Naor Dalal, Yossi Oren, Yuval Dorfan, Jonathan Giron, Rami Puzis
Appeared in: Cyberbiosecurity
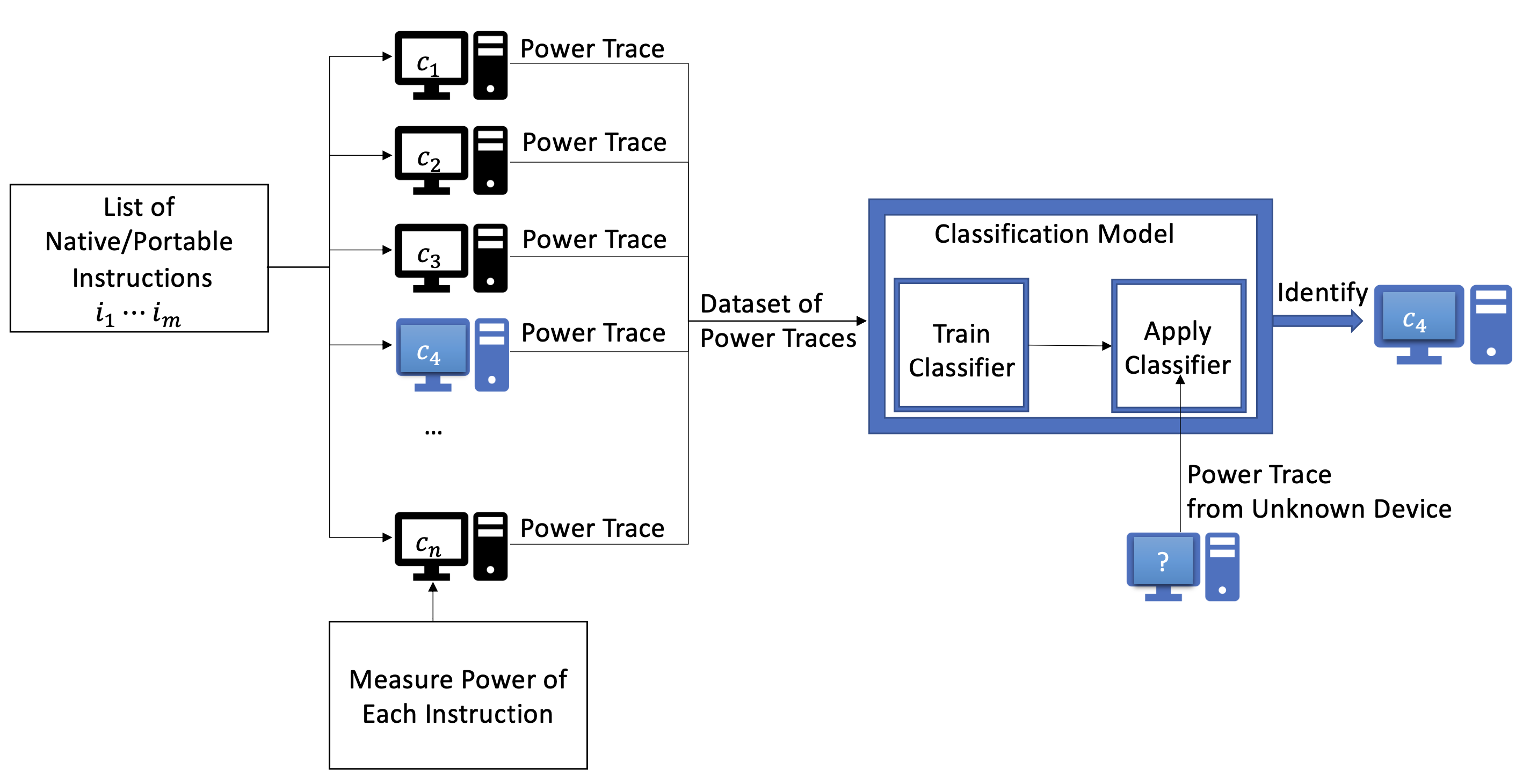
The Finger in the Power: How to Fingerprint PCs by Monitoring their Power Consumption
Authors: Marina Botvinnik, Tomer Laor, Thomas Rokicki, Clémentine Maurice, Yossi Oren
Appeared in: 20th Conference on Detection of Intrusions and Malware & Vulnerability Assessment, DIMVA 2023
Juliet-PUF: Enhancing the Security of IoT-Based SRAM-PUFs Using the Remanence Decay Effect
Authors: Amit Kama, Michael Amar, Snir Gaaton, Kang Wang, Yifan Tu, Yossi Oren
Appeared in: IEEE Internet of Things Journal Volume 10, Issue 14, July 2023
Characterization and Detection of Cross-Router Covert Channels
Authors: Oren Shvartzman, Adar Ovadya, Kfir Zvi, Omer Shwartz, Rom Ogen, Yakov Mallah, Niv Gilboa, Yossi Oren
Appeared in: Elsevier Computers & Security, January 2023, 103125
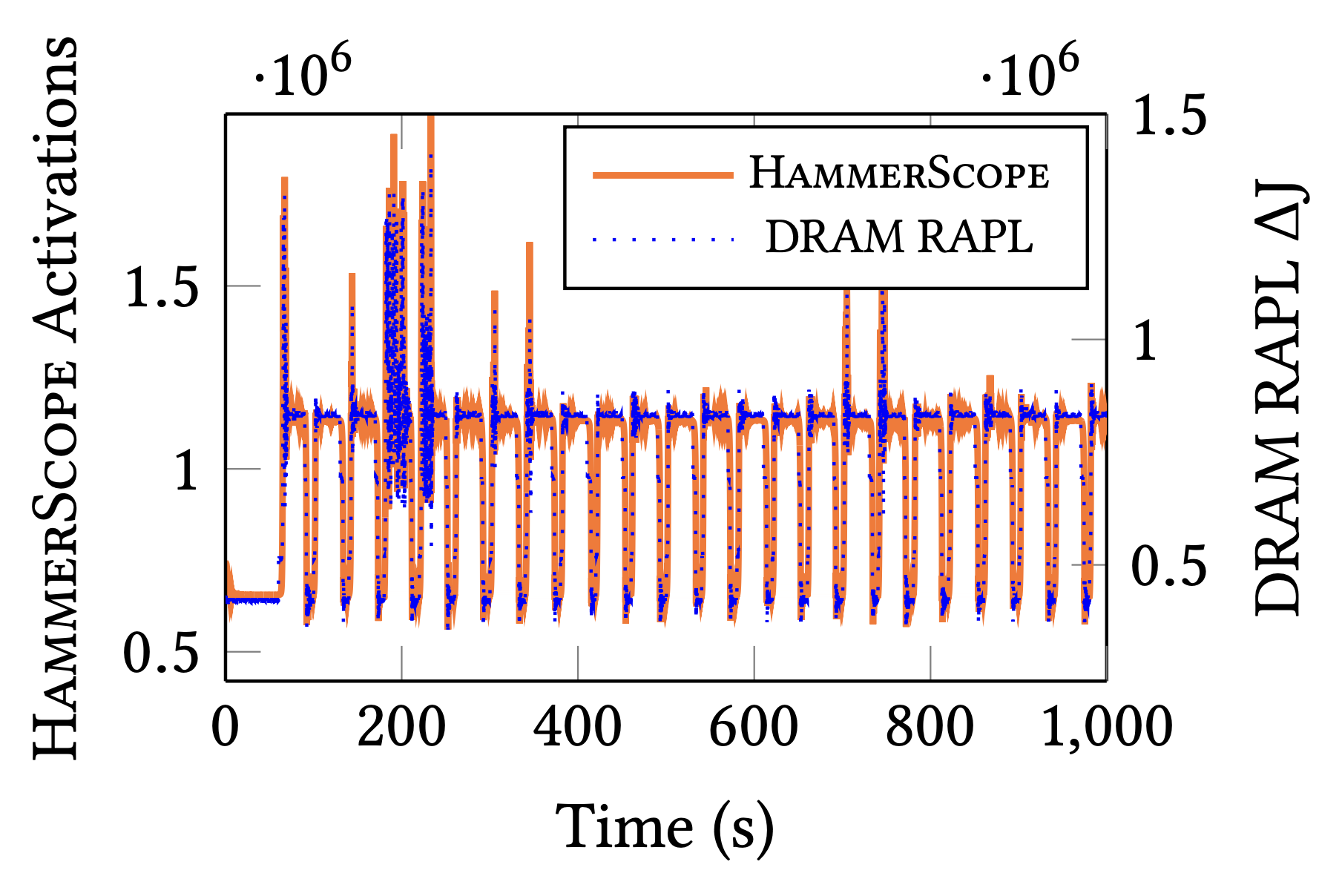
HammerScope: Observing DRAM Power Consumption Using Rowhammer
Authors: Yaakov Cohen, Kevin Sam Tharayil, Arie Haenel, Daniel Genkin, Angelos D. Keromytis, Yossi Oren, Yuval Yarom
Appeared in: 29th ACM Conference on Computer and Communications Security (CCS), 2022
Port Contention Goes Portable: Port Contention Side Channels in Web Browsers
Authors: Thomas Rokicki, Clémentine Maurice, Marina Botvinnik, Yossi Oren
Appeared in: 17th ACM ASIA Conference on Computer and Communications Security, AsiaCCS 2022
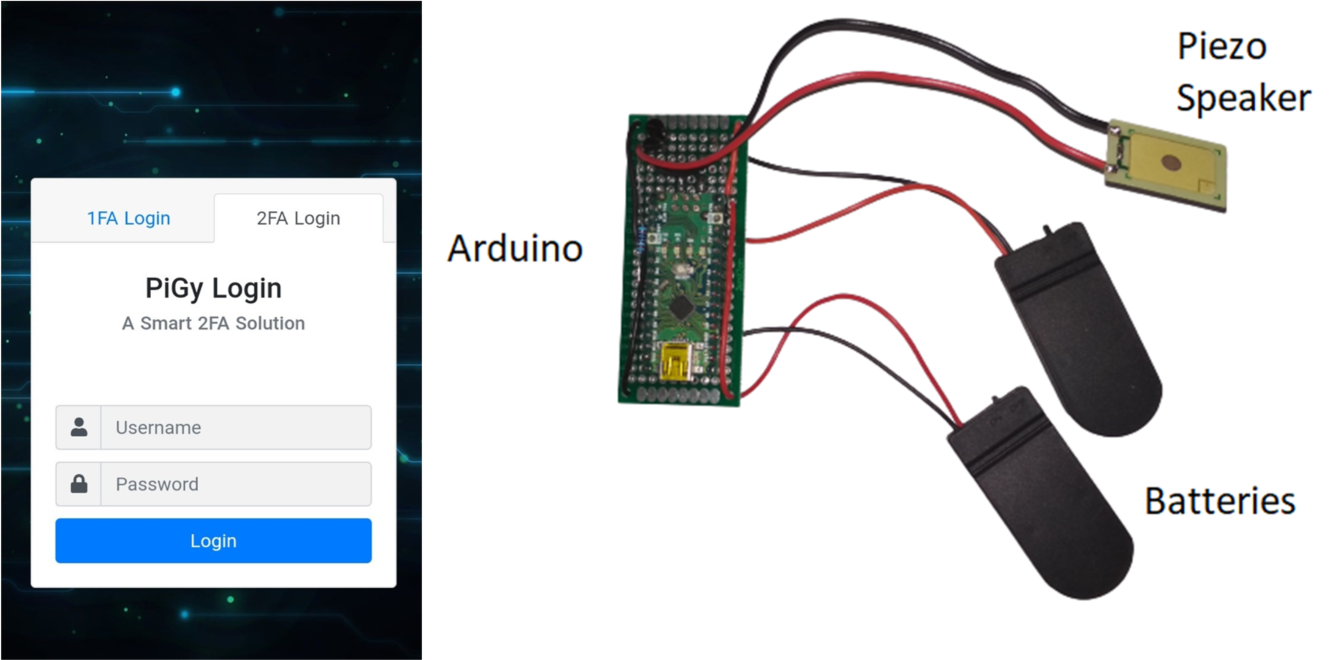
Toward Usable and Accessible Two-Factor Authentication Based on the Piezo-Gyro Channel
Authors: Dan Arad, Yossi Oren
Appeared in: IEEE Access, Volume 10, 2022
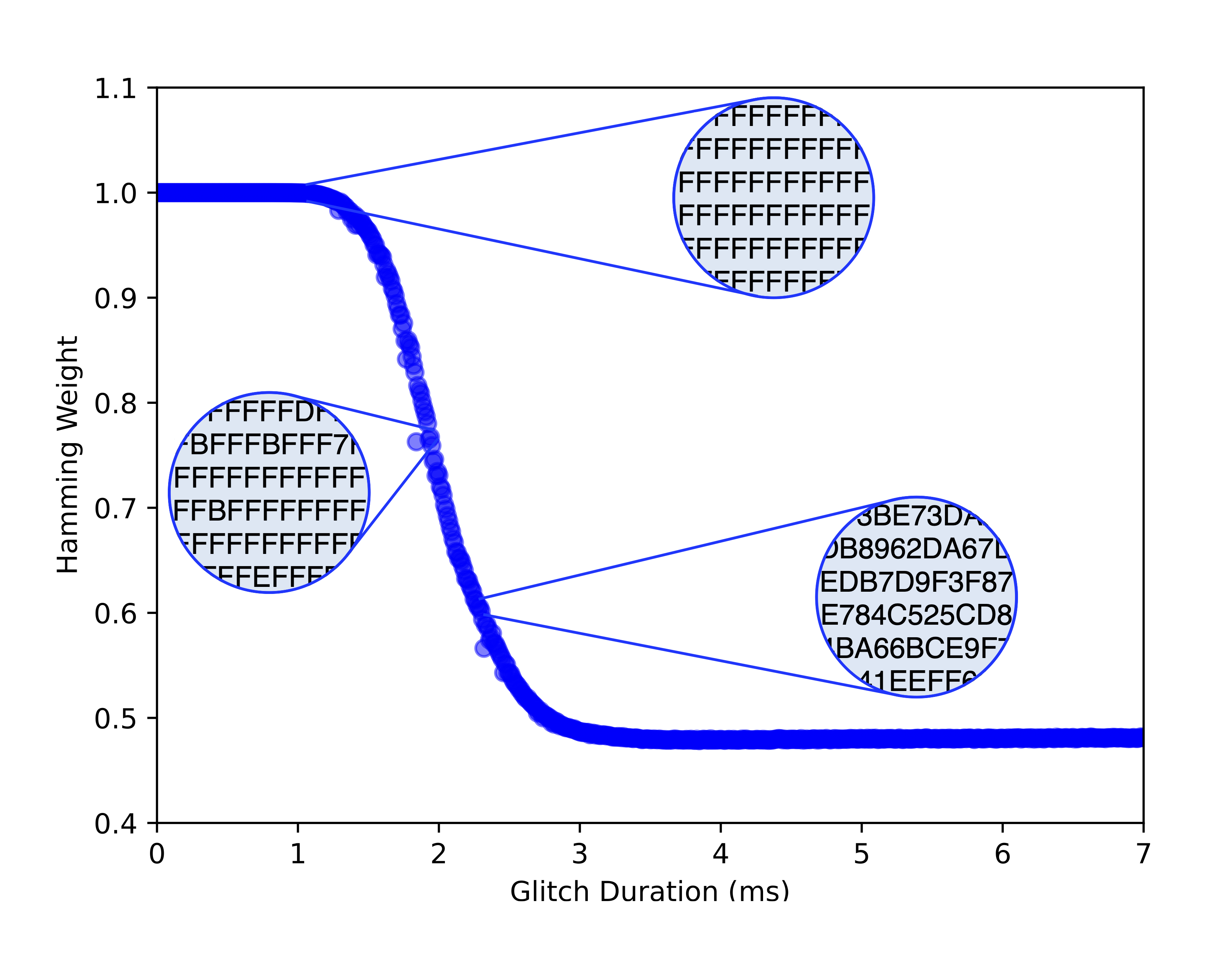
Practical, Low-Cost Fault Injection Attacks on Personal Smart Devices
Authors: Shaked Delarea, Yossi Oren
Appeared in: Applied Sciences, Volume 12 Issue 1, 2022
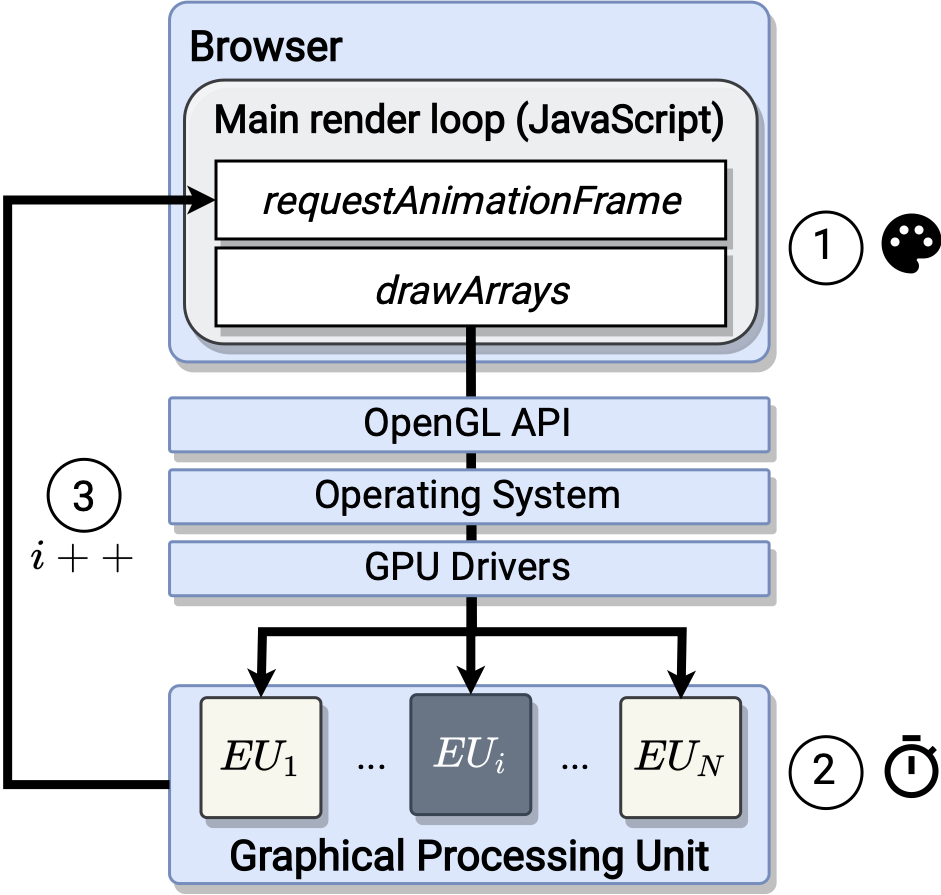
DRAWN APART : A Device Identification Technique based on Remote GPU Fingerprinting
Authors: Tomer Laor, Naif Mehanna, Vitaly Dyadyuk, Antonin Durey, Pierre Laperdrix, Clémentine Maurice, Yossi Oren, Romain Rouvoy, Walter Rudametkin, Yuval Yarom
Appeared in: 29th Annual Network and Distributed System Security Symposium, NDSS 2022
Cache-based characterization: A low-infrastructure, distributed alternative to network-based traffic and application characterization
Authors: Anatoly Shusterman, Chen Finkelstein, Ofir Gruner, Yarin Shani, Yossi Oren
Appeared in: Elsevier Computer Networks Volume 200, December 2021
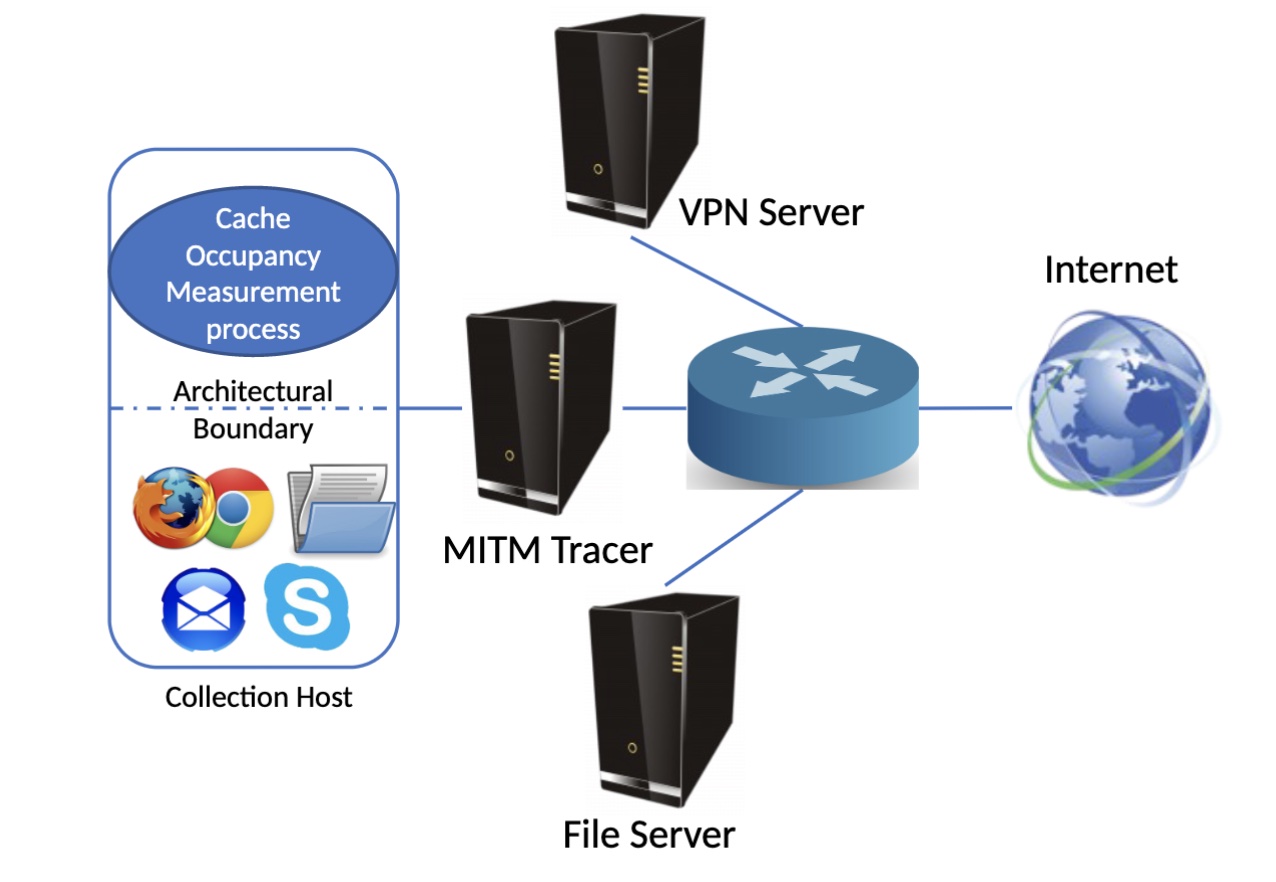
Website Fingerprinting Through the Cache Occupancy Channel and its Real World Practicality
Authors: Anatoly Shusterman, Zohar Avraham, Eliezer Croitoru, Yarden Haskal, Lachlan Kang, Dvir Levi, Yosef Meltser, Prateek Mittal, Yossi Oren, Yuval Yarom
Appeared in: IEEE Transactions on Dependable and Secure Computing Volume 18, Issue 5, September 2021
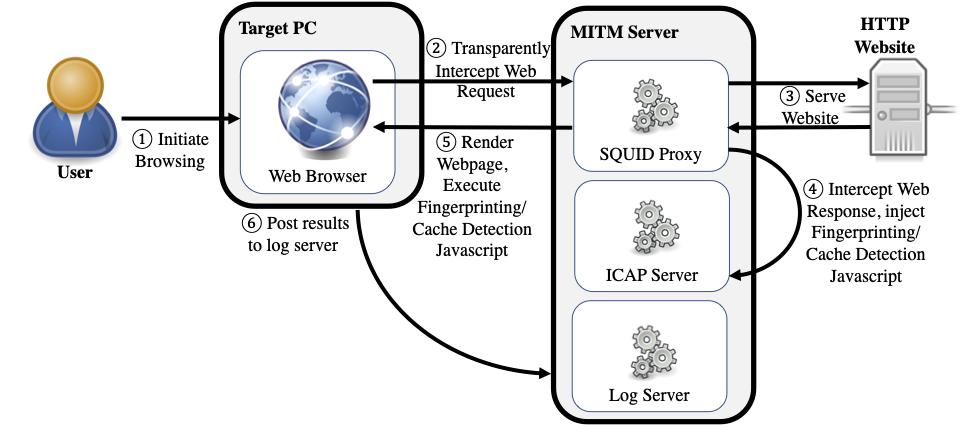
Prime+Probe 1, JavaScript 0: Overcoming Browser-based Side-Channel Defenses
Authors: Anatoly Shusterman, Ayush Agarwal, Sioli O’Connell, Daniel Genkin, Yossi Oren, Yuval Yarom
Appeared in: 30th USENIX Security Symposium, 2021
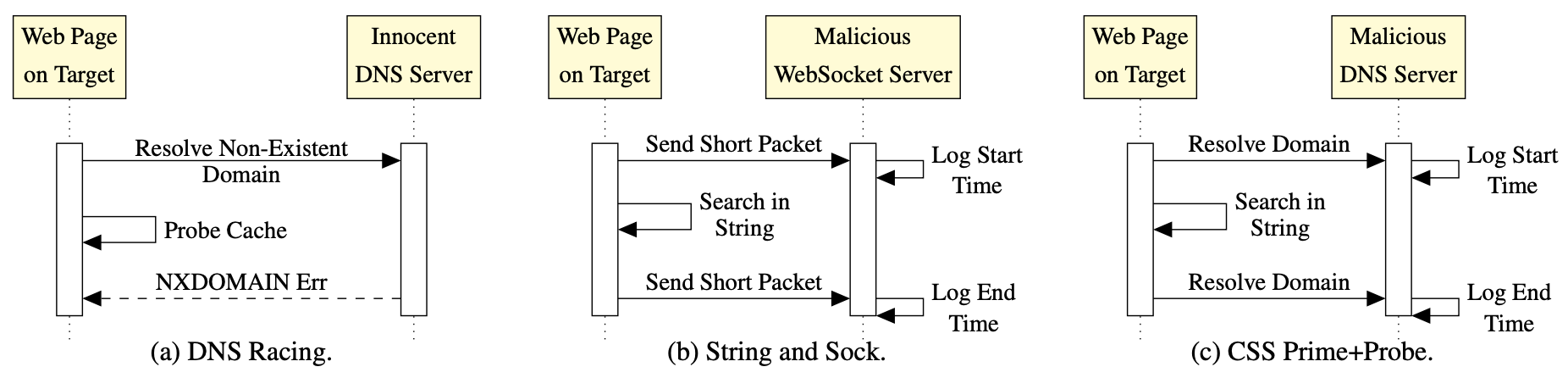
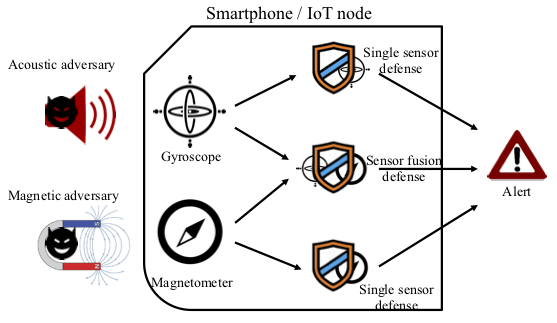
Sensor Defense In-Software (SDI): Practical Defenses Against Spoofing Attacks on Position Sensors
Authors: Kevin Sam Tharayil, Benyamin Farshteindiker, Shaked Eyal, Nir Hasidim, Roy Hershkovitz, Shani Houri, Ilia Yoffe (Iofedov), Michal Oren, Yossi Oren
Appeared in: Engineering Applications of Artificial Intelligence Volume 95, 2020
Can the Operator of a Drone Be Located by Following the Drone’s Path?
Authors: Eliyahu Mashhadi, Yossi Oren, Gera Weiss
Appeared in: 4th International Symposium on Cyber Security Cryptography and Machine Learning, 2020
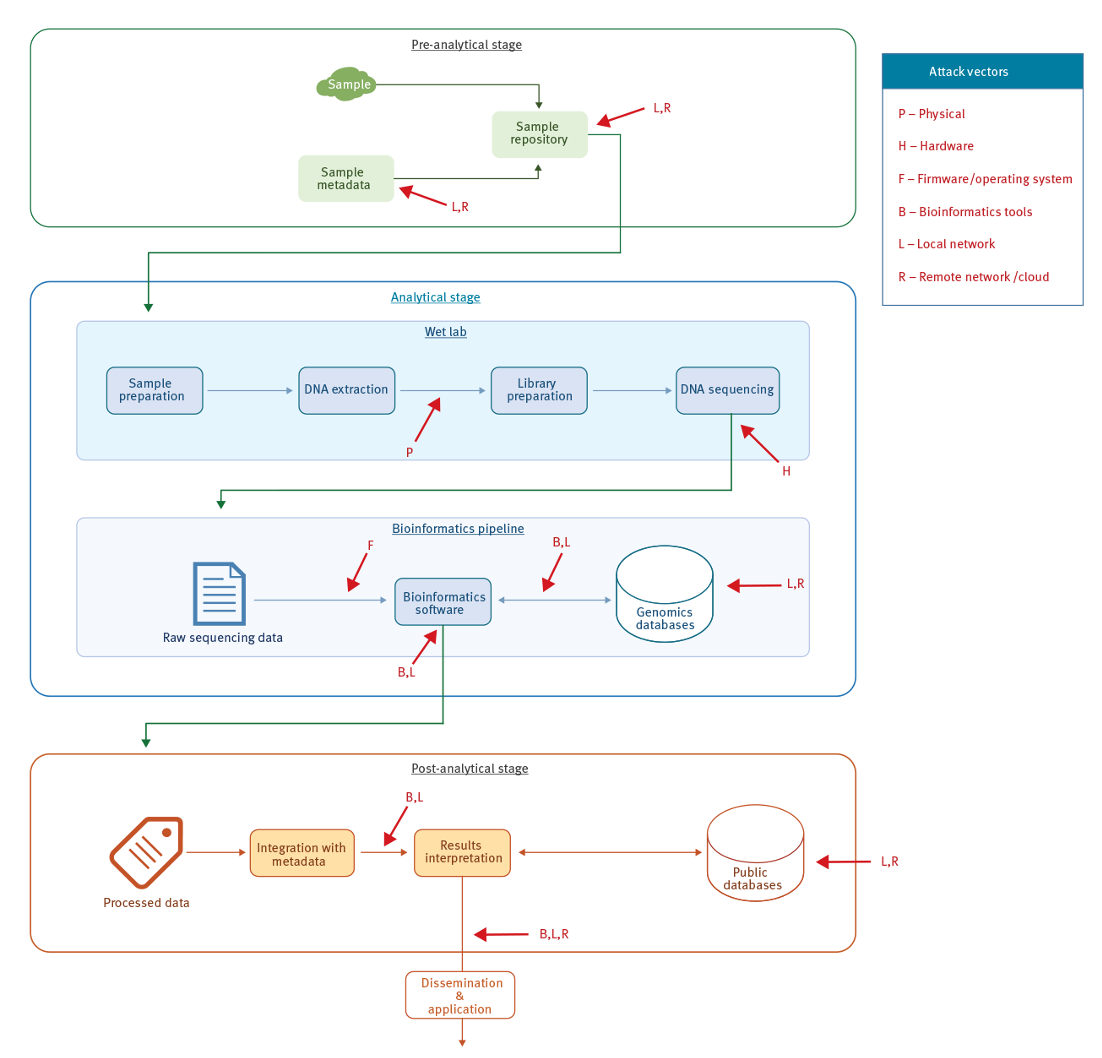
Cyber Security Threats in the Microbial Genomics Era: Implications for Public Health
Authors: Iliya Fayans, Yair Motro, Lior Rokach, Yossi Oren, Jacob Moran-Gilad
Appeared in: Eurosurveillance Volume 25, Issue 6, 2020
Inner Conflict: How Smart Device Components Can Cause Harm
Authors: Omer Shwartz, Amir Cohen, Asaf Shabtai, Yossi Oren
Appeared in: Elsevier Computers & Security, Volume 89, February 2020, 101665
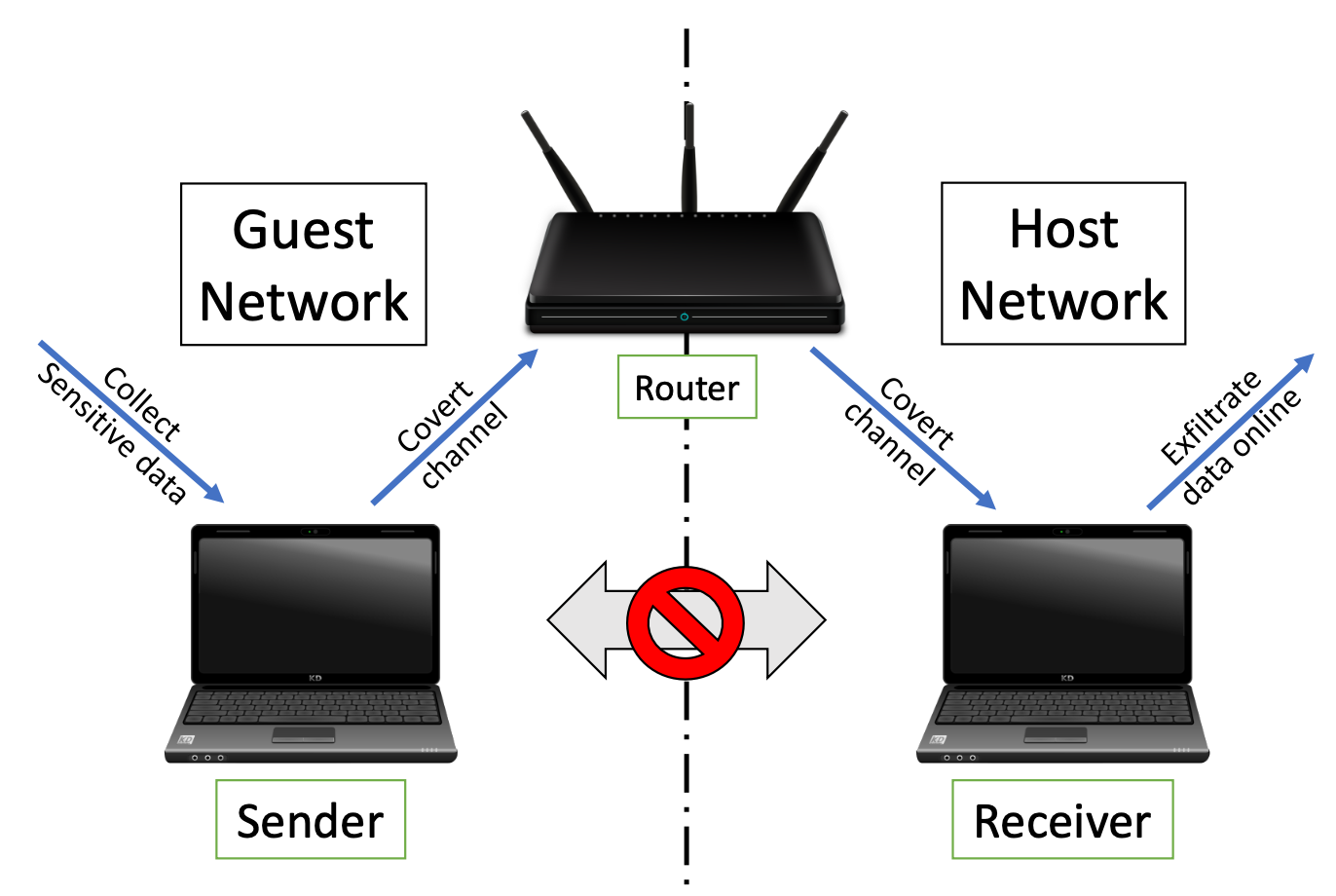
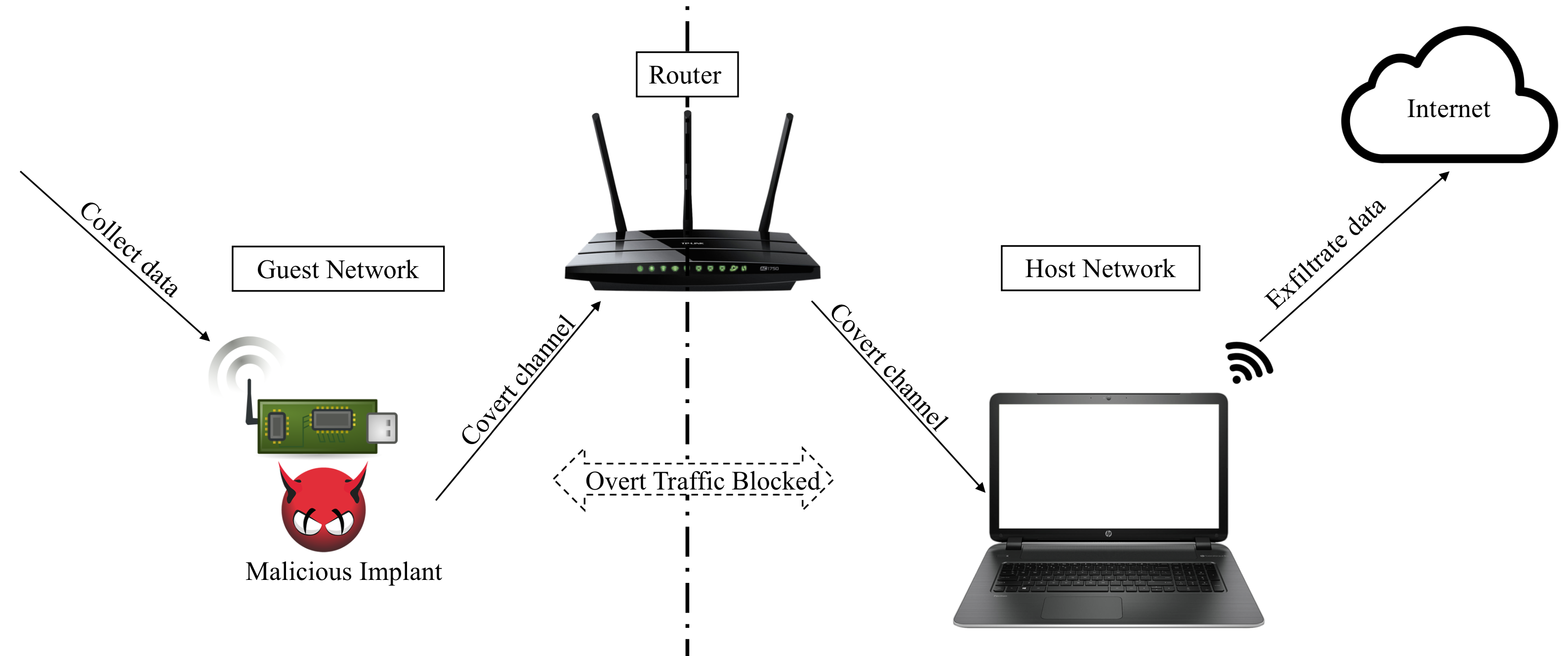
Cross-Router Covert Channels
Authors: Adar Ovadya, Rom Ogen, Yakov Mallah, Niv Gilboa, Yossi Oren
Appeared in: 13th USENIX Workshop on Offensive Technologies (WOOT), 2019
Cyber Attack on SUUNTO Dive Computer
Authors: Sofia Dimant, Maya Kremer, Omer Shwartz, Yossi Oren
Appeared in: Technical Report
Robust Website Fingerprinting Through the Cache Occupancy Channel
Authors: Anatoly Shusterman, Lachlan Kang, Yarden Haskal, Yosef Meltser, Prateek Mittal, Yossi Oren, Yuval Yarom
Appeared in: 28th USENIX Security Symposium, 2019
Reverse Engineering IoT Devices: Effective Techniques and Methods
Authors: Omer Shwartz, Yael Mathov, Michael Bohadana, Yuval Elovici, Yossi Oren
Appeared in: IEEE Internet of Things Journal, Volume 5, Issue 6, 2019
Sensorless, Permissionless Information Exfiltration with Wi-Fi Micro-Jamming
Authors: Rom Ogen, Omer Shwartz, Kfir Zvi, Yossi Oren
Appeared in: 12th USENIX Workshop on Offensive Technologies (WOOT), 2018
Brief Announcement: Deriving Context for Touch Events
Authors: Moran Azran, Niv Ben Shabat, Tal Shkolnik, Yossi Oren
Appeared in: Second International Symposium on Cyber Security Cryptography and Machine Learning (CSCML), 2018

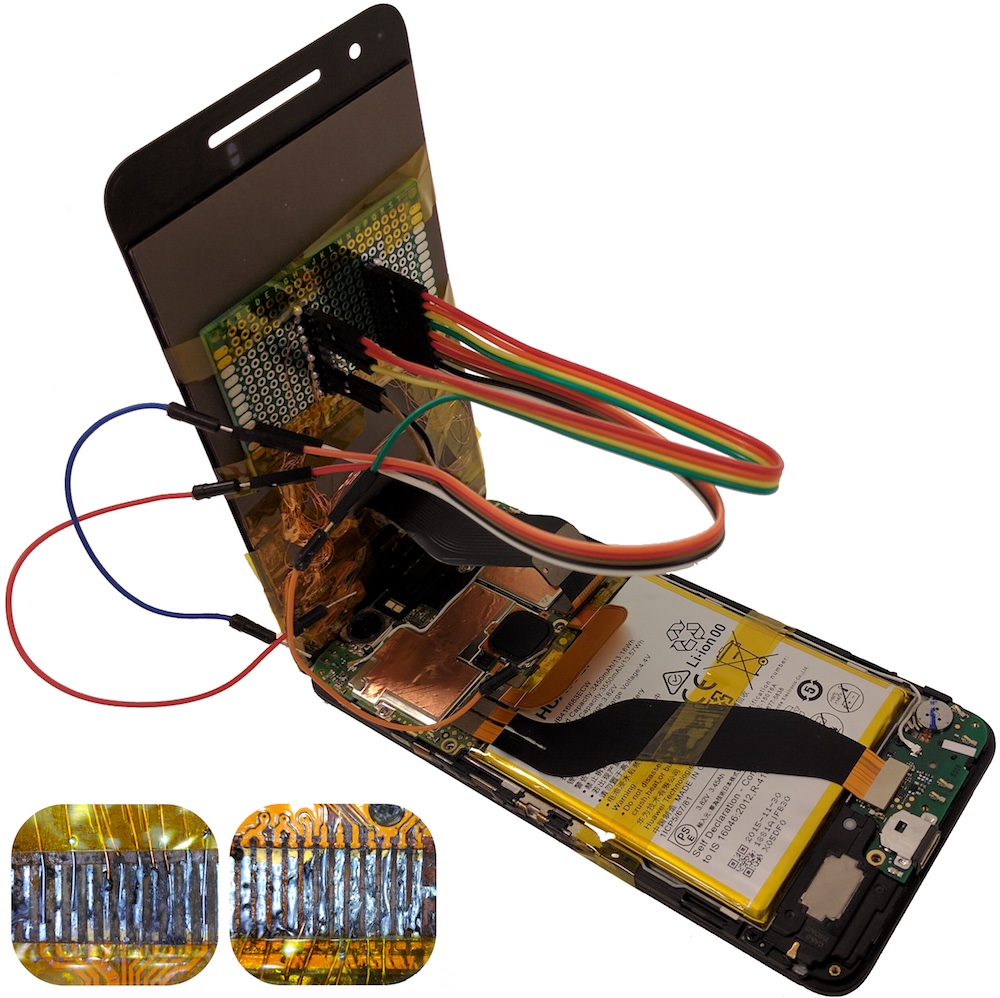
Shattered Trust: When Replacement Smartphone Components Attack
Authors: Omer Shwartz, Amir Cohen, Asaf Shabtai, Yossi Oren
Appeared in: 11th USENIX Workshop on Offensive Technologies (WOOT), 2017

Opening Pandora's Box: Effective Techniques for Reverse Engineering IoT Devices
Authors: Omer Shwartz, Yael Mathov, Michael Bohadana, Yuval Elovici, Yossi Oren
Appeared in: 17th Smart Card Research and Advanced Application Conference (CARDIS), 2017
From Smashed Screens to Smashed Stacks: Attacking Mobile Phones Using Malicious Aftermarket Parts
Authors: Omer Shwartz, Guy Shitrit, Asaf Shabtai, Yossi Oren
Appeared in: Workshop on Security for Embedded and Mobile Systems (SEMS), 2017
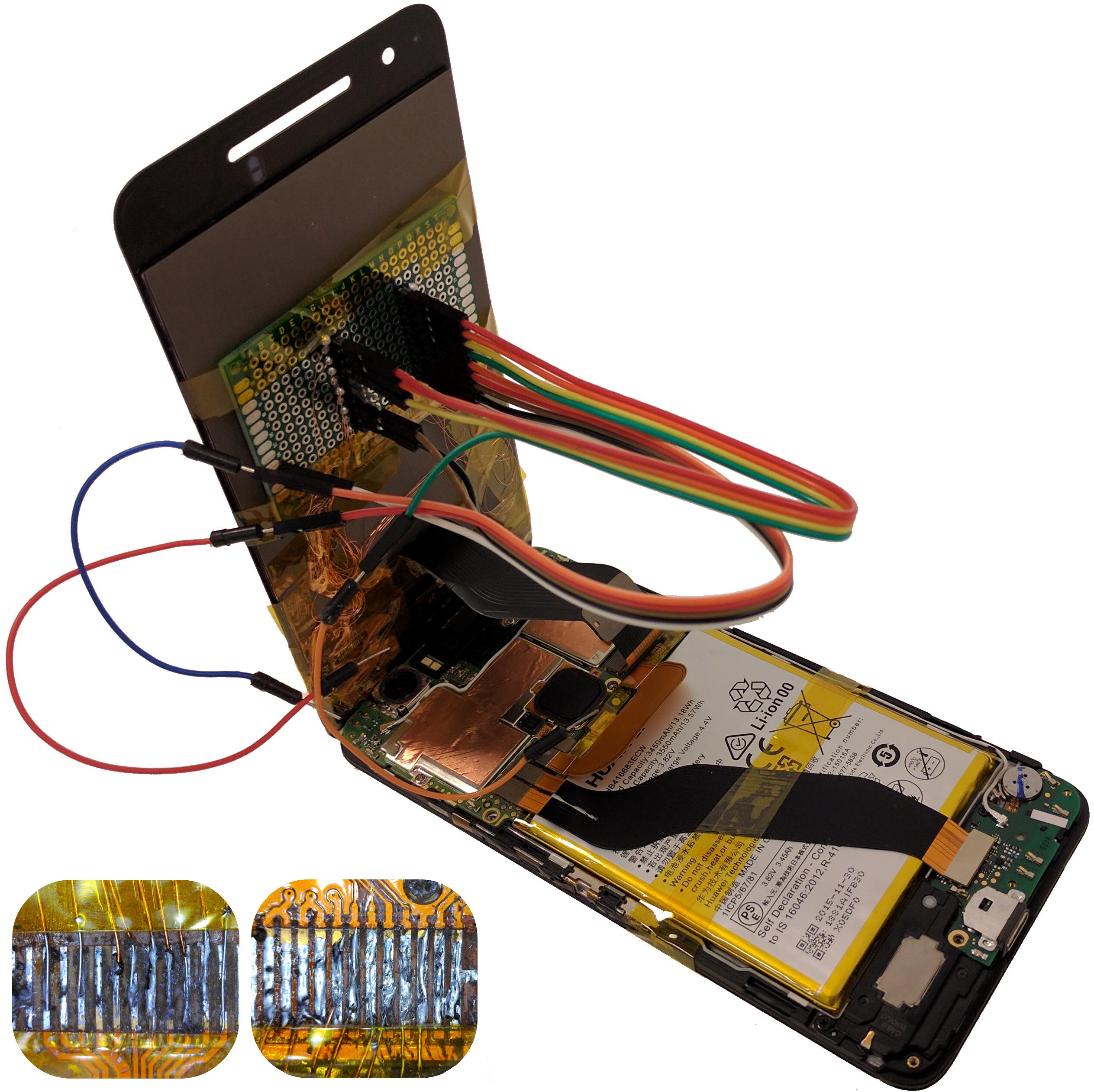
The Curious Case of the Curious Case: Detecting touchscreen events using a smartphone protective case
Authors: Tomer Gluck, Rami Puzis, Yossi Oren, Asaf Shabtai
Appeared in: Workshop on Security for Embedded and Mobile Systems (SEMS), 2017
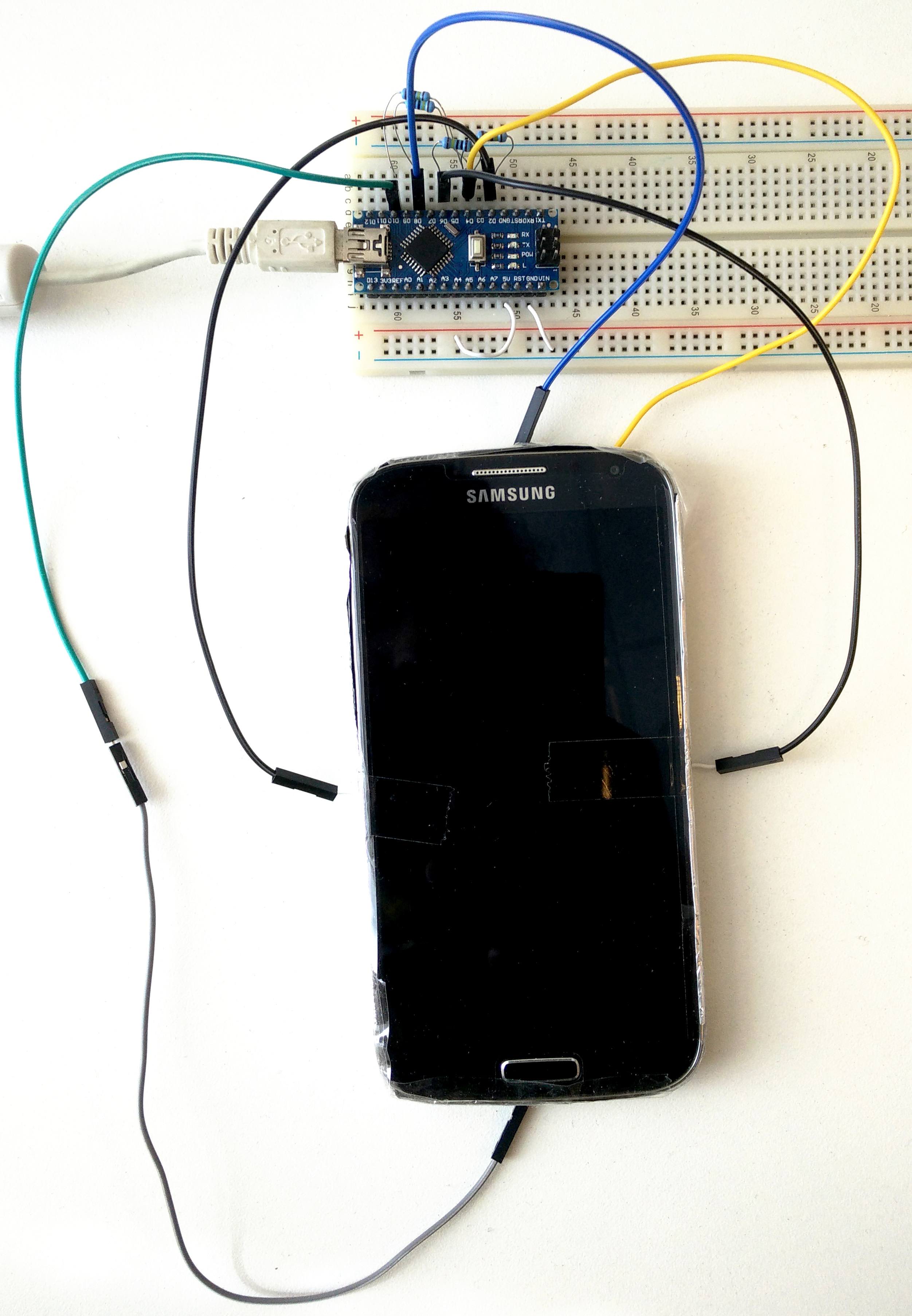
How to Phone Home with Someone Else's Phone: Information Exfiltration Using Intentional Sound Noise on Gyroscopic Sensors
Authors: Benyamin Farshteindiker, Nir Hasidim, Asaf Grosz, Yossi Oren
Appeared in: 10th USENIX Workshop on Offensive Technologies (WOOT), 2016